New year, new NorzhCTF edition, organized next to the FIC 2020. As I am no longer student at ENSIBS, I had the opportunity to participate in the event. This post deals with the solution of “Familly Business”, an OSINT/SOCMINT challenge divided in 2 parts.
The challenge is mainly around social media but also deals with a slightly more technical part. Before starting, I have to say that some part are not really OSINT as long as 2 intrusions are necessary.
Index
Initial statement
We have doubts that Mr. Lukas DUMMAS, the former CISO of Norzh Nuclea, sold protected company information to a family member and representative of a foreign power. We ask you to investigate!
The first flag will be on a server owned by Lukas. The second will be in the files exchanged with the foreign power.
Familly Business 1
We know that the first flag is supposed to be on a Mr.DUMMAS’s server. Little bit unclear.. But ok, let’s go !
Having very vew informations about the target, my first reflex was googling the name. Simple request allows us to retrieve a LinkedIn profile.
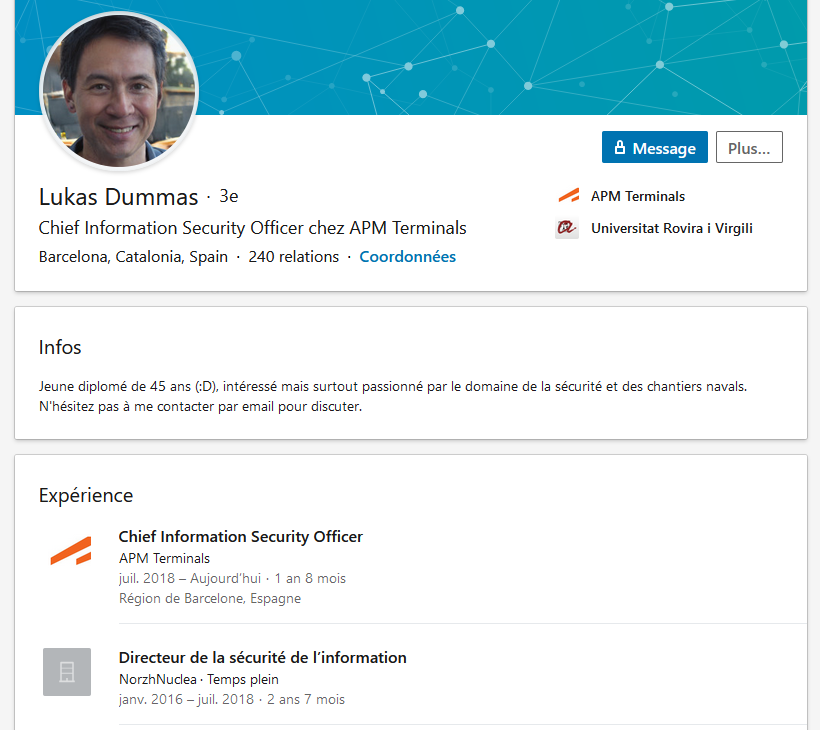
This allows us to learn more about the life of Lukas DUMMAS, but also puts a potential face on this identity. On the other hand, we can also retrieve an e-mail address belonging to him. Right now, it is not possible to know we will have to use it or no.
After some research on other Google’s results (for example, the Apollo.io link), we start using Google Dorks in order to filter results. The first one, quite simple, already give interesting results.
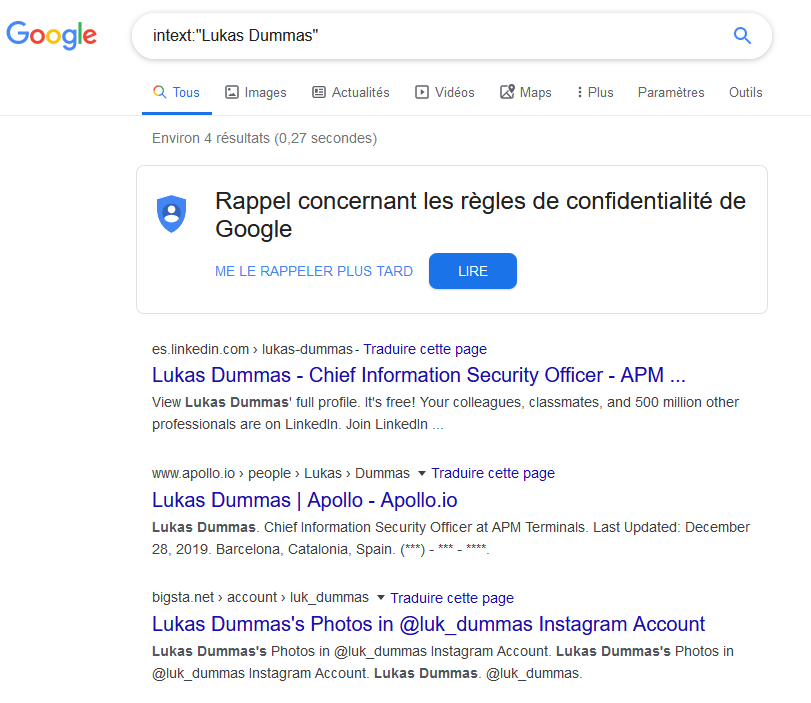
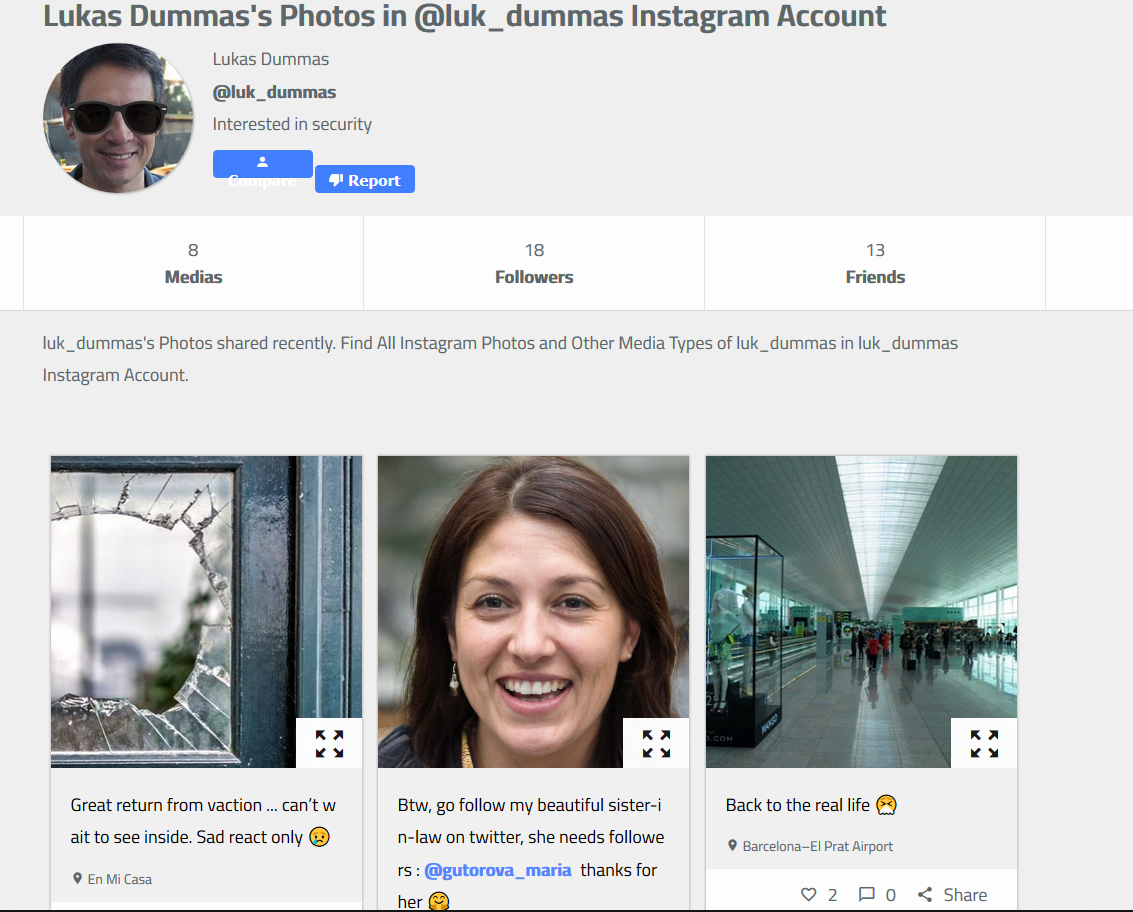
Using this, we can get one Instagram account, which seems to be owned by M.DUMMAS. Profile analysis reveals two interesting things :
- A username ;
- A woman picture, in a post stating that this is Lukas’s sister-in-law (usefull later!)
A simple Google query with the username bring a Twitter profile/a>. Same username, visual elements linked to a spanish people… It seems that this profile is also owned by the target.
A quick account analysis reveals an interesting tweet, to the OVH company and containing network logs. If we look as the screenshot, we can see a bunch of IP addresses. Keeping in mind that M.DUMMAS is a former CISO, these elements could lead us to his server.
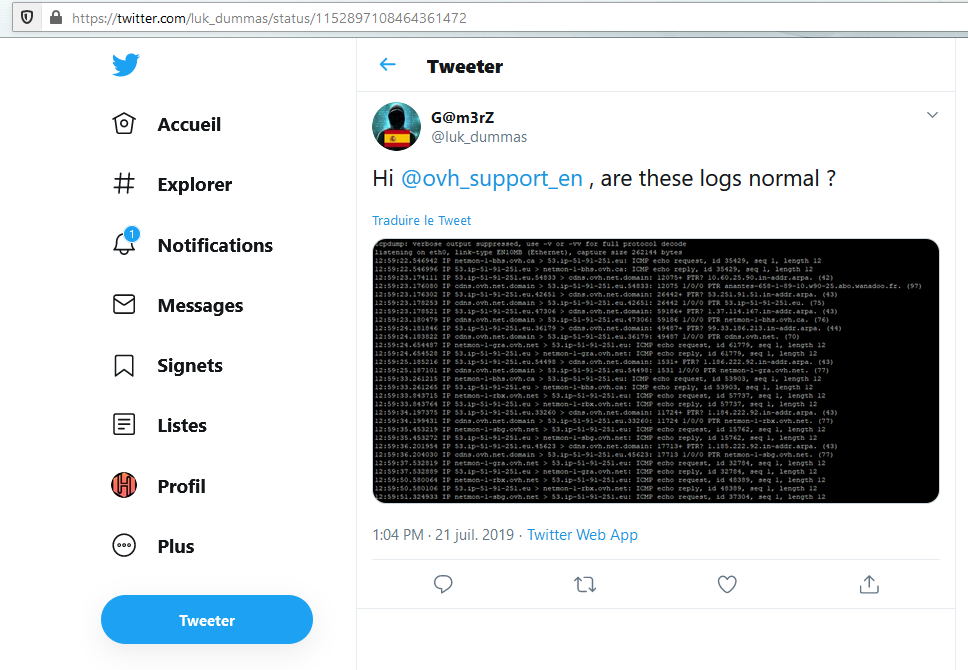
So, we extract all the potential IP addresses and using tools like Shodan, we can start investigation. Nothing interesting until this one : 51.91.251.53
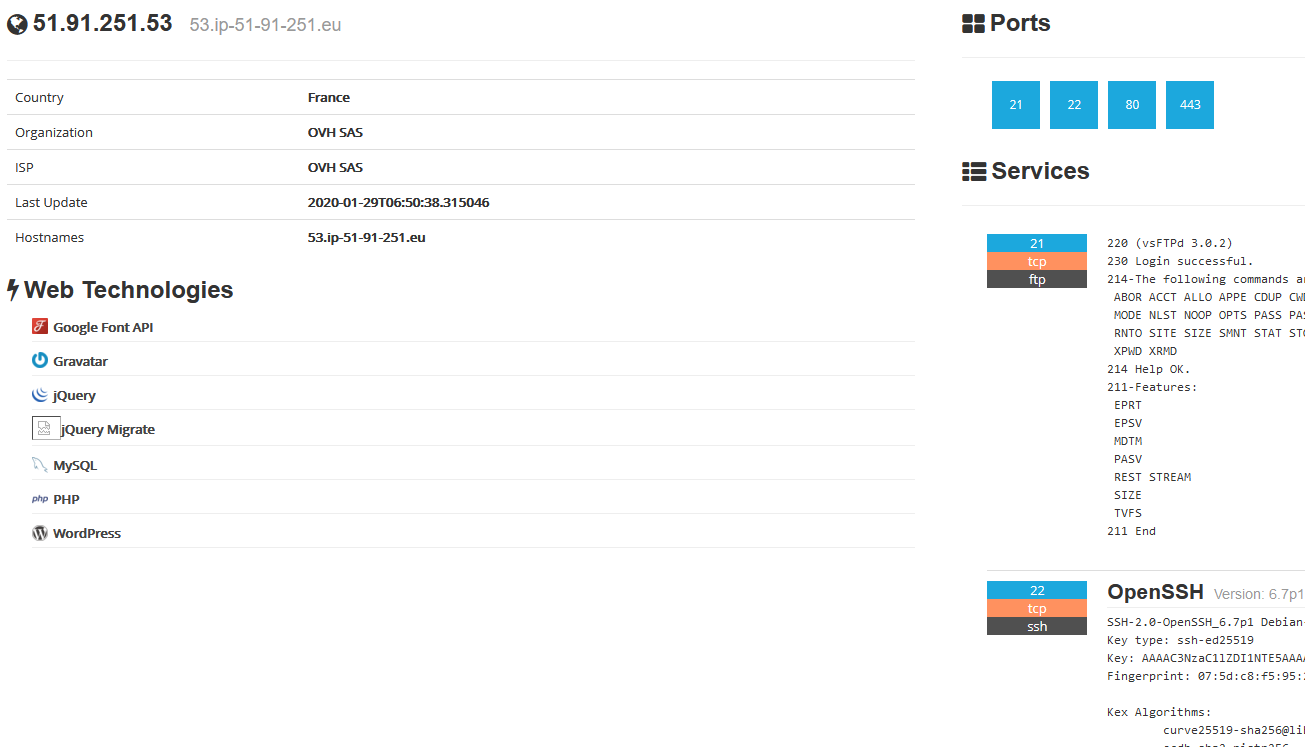
Indeed, it seems that this one correspond to a server hosted by OVH. Furthermore, 4 potentials ports are opened, and especially the 80 and 443 (HTTP and HTTPS)
Let’s check if any application web is responding on the server. We first get a “Let’s Encrypt” SSL certificate. It’s quite good as long as in the case of personnal websites, you can often see that kind of certificate because it’s easy to deploy and affordable. Then, the user is redirected to the Lukas’s Wordpress website.
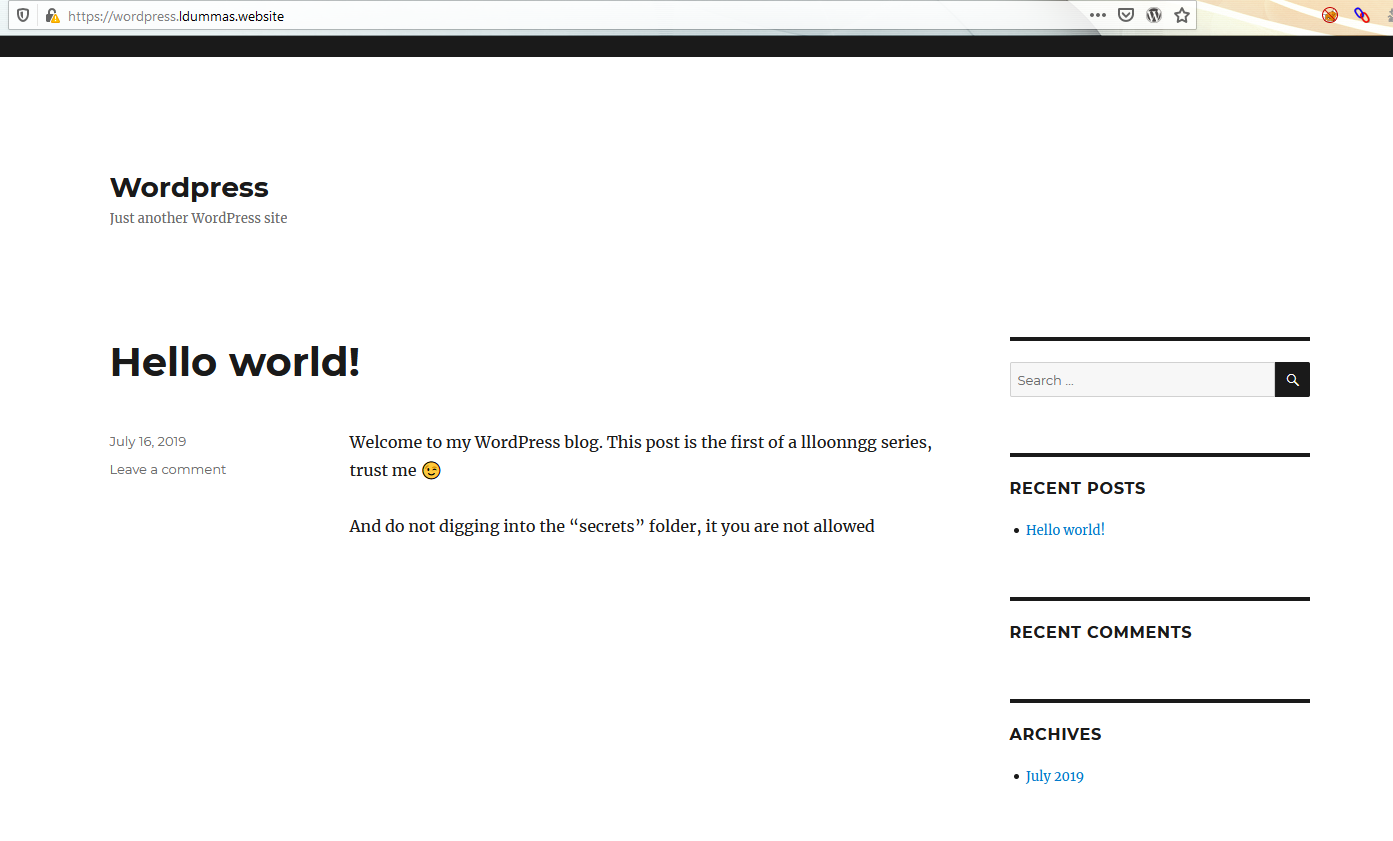
A suspicious message warns users :
"And do not digging into the “secrets” folder, it you are not allowed"
Thus, we try to access resources like “/secrets”, no results. From there, my personnal experience is telling me to do content discovery by fuzzing the application. But that’s only after some tries, and some time, we realize that the solution was way more simple…
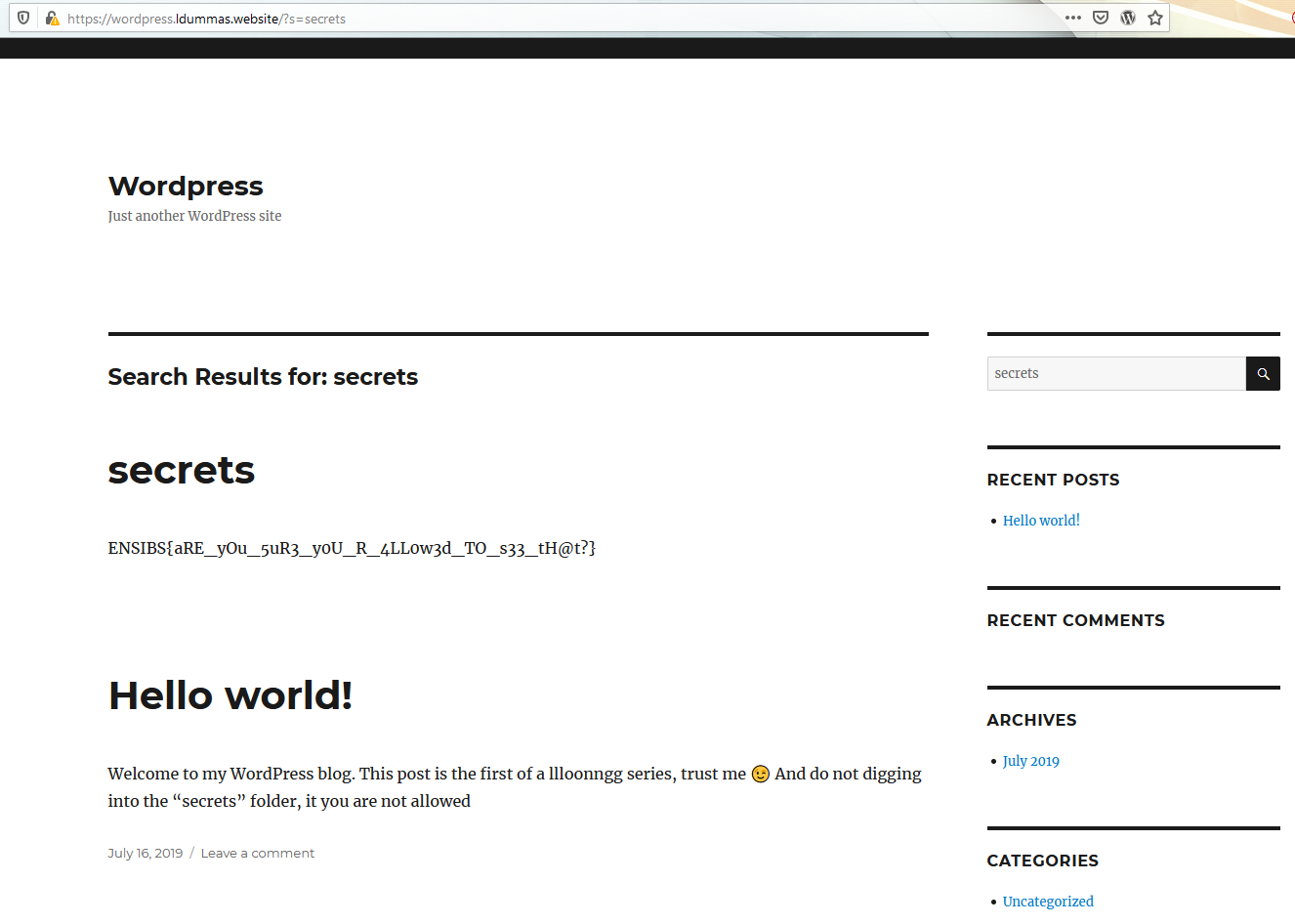
A simple query and we grab the first flag !
Familly Business 2
For the second challenge, the initial statement tells that the flag is inside “shared files with the foreign country”.
Alright. Looking at the statement, we start to investigate on the target familly member. We previously identified “Maria Gutorova” who seems to be the target’s sister-in-law. Through the first Instagram account, the target is telling that his sister-in-law should have more Twitter followers, and he gives a username (link).
Note : The account is also existing on Instagram, but is owned by a real person… Which cost me some minutes of false positive during the challenge :(

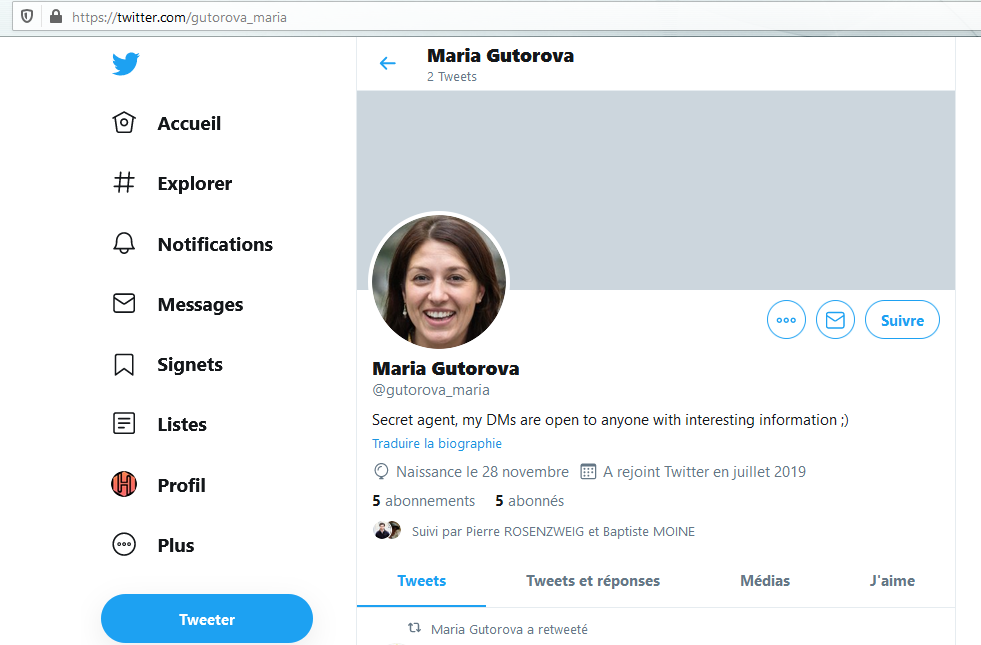
From then, some time has passed before getting another good element. Indeed, we lack some new informations. No problem, we can go back to already known things and analyze everything. First, we go back to the initial target Twitter’s account.
After some investigation, we face 2 interesting tweets (here and here).
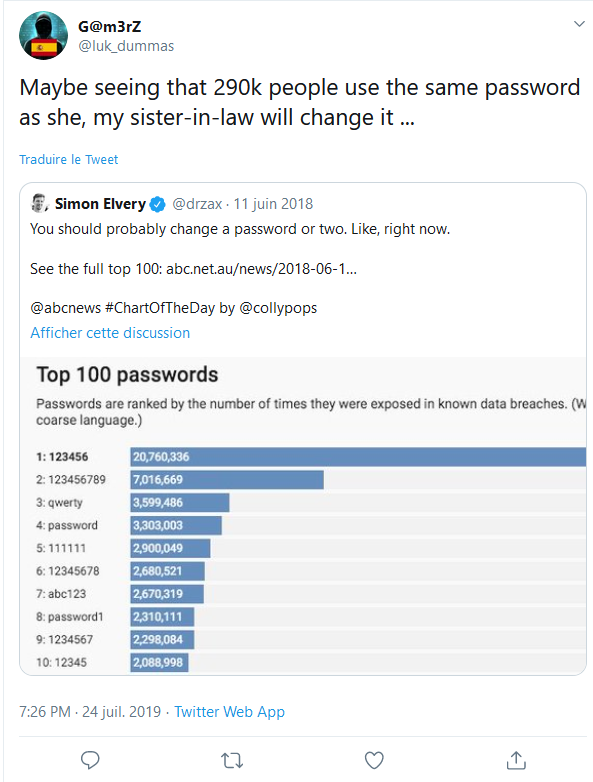
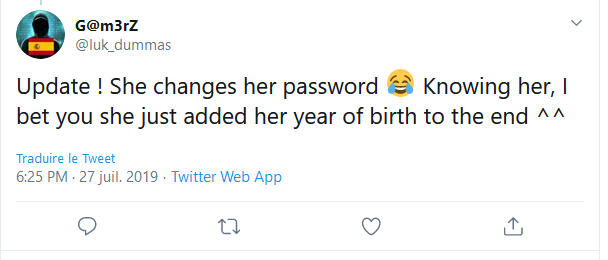
The first leads to a ranking of the most used passwords, followed by a message from Lukas explaining that 290,000 people are using the same password as his sister-in-law. The second tweet states that Maria would have updated her password but that, knowing her, she would only have added her year of birth.
Ok, even if it’s out of a purely OSINT context, the instructions are pretty clear : we need to find the password for Maria’s Twitter account.
If we stick to the ranking, the password used by 290,000 people is: FQRG7CS493
There’s still an unknown part, Maria’s date of birth. Her Twitter account indicates a birth on “November 28th”, but the year is not displayed…
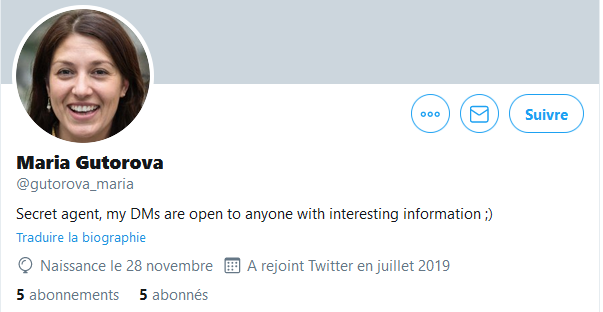
This is where you will find a little trick from Twitter that allows you to set the amount of information displayed to different types of users. Thus, for an average person, with or without an account, only the day and month of birth will be displayed. On the other hand, if you follow the account, then the complete date will be displayed. Using a lambda account, we can retrieve the year of birth of this second target, 1980.
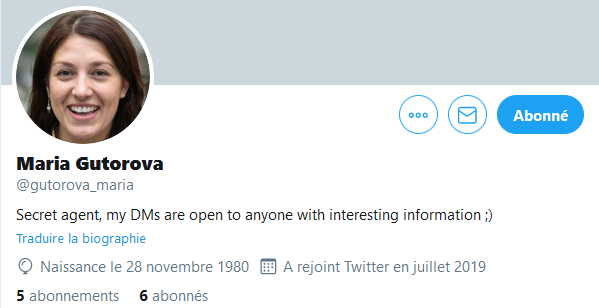
We don’t have Maria’s e-mail address but Twitter allows user to log in with their username. We can then rebuild the password (FQRG7CS4931980) and log in !
Then, we go straight forward to the DM (Direct Messages). We can find a conversation between Maria and Lukas, telling that some “informations” are stored on the Luka’s private server. Moreover, a password is sent.
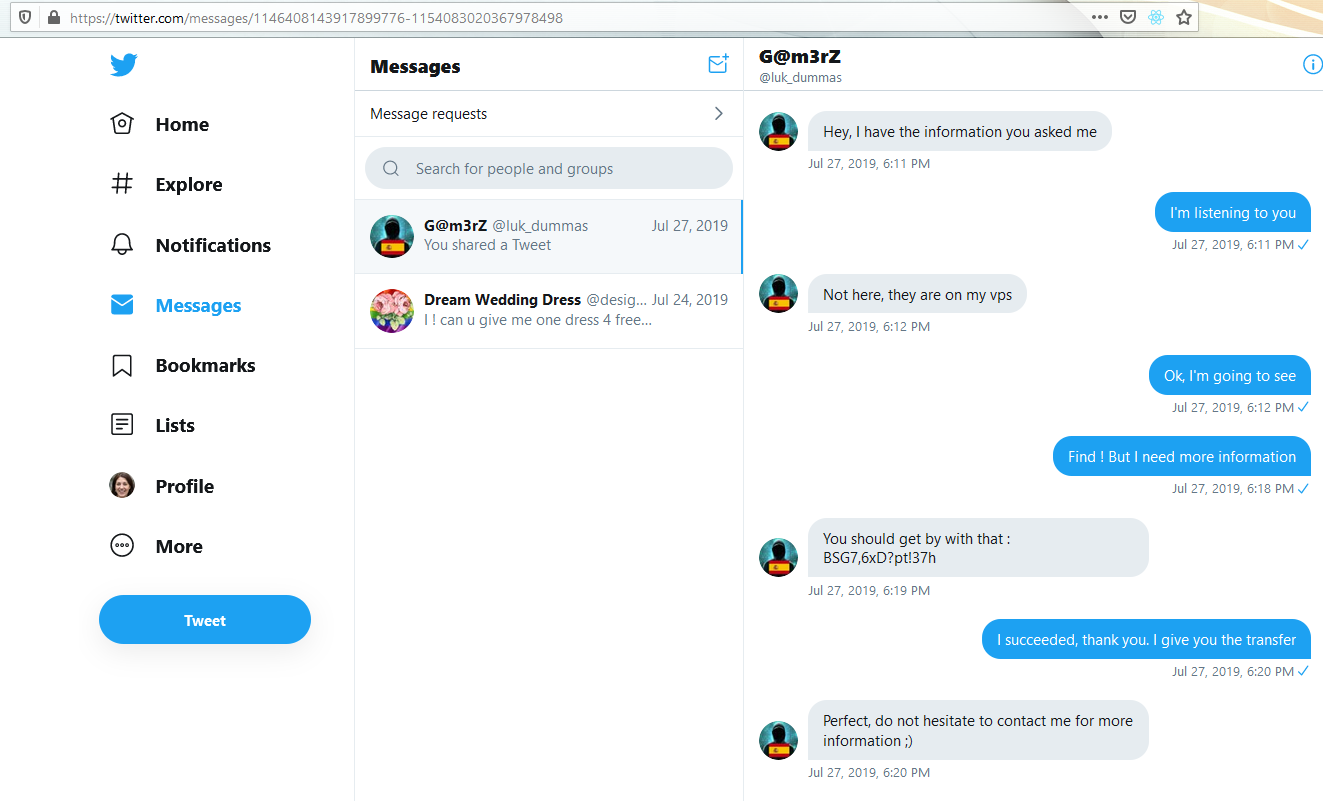
Bakc to what we previously saw, we only found one server owned by Lukas (51.91.251.53). Remember, 4 ports were open, with 4 potentials service… And one FTP server !
One of the most common mistakes on this kind of server is to let the anonymous log in active. Alright, we fire up FileZilla and we can try this.
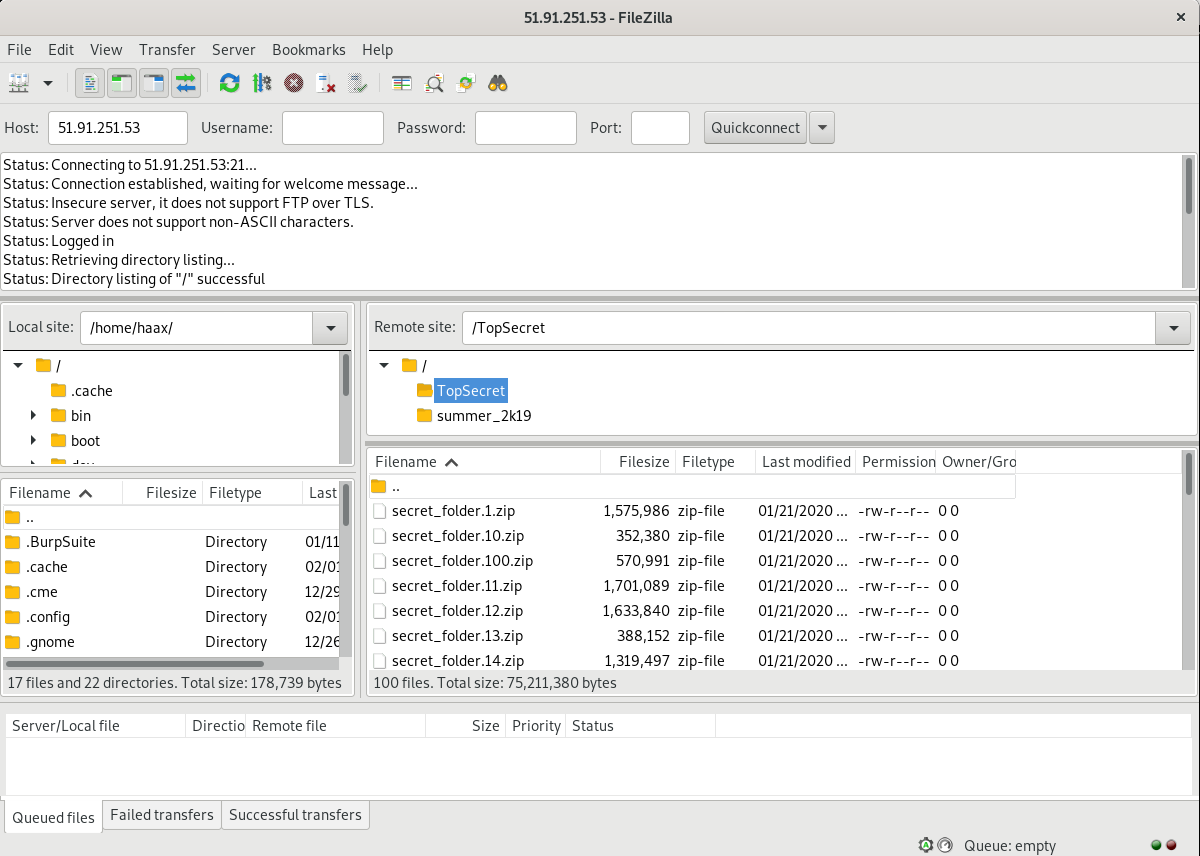
B00m ! It works ! We have now access to dozens of files. In order to be sure to have everything, we dump the entire server locally, for offline analysis.
We realize quite quickly that ZIP files are encrypted. So, we need the password to read them. Maybe could it be the password sent by Lukas to Maria on their Twitter conversation ?
A quick bash loop shows that only one archive can be decrypted using the given password
$ for i in {0..100}; do unzip -P 'BSG7,6xD?pt!37h' secret_folder.$i.zip; done
unzip: cannot find or open secret_folder.0.zip, secret_folder.0.zip.zip or secret_folder.0.zip.ZIP.
[...]
Archive: secret_folder.81.zip
skipping: secret_file.81 incorrect password
Archive: secret_folder.82.zip
inflating: secret_file.82
Archive: secret_folder.83.zip
skipping: secret_file.83 incorrect password
[...]
We then get a 193Mo ASCII file, displaying thousands of the same string. Let’s base64 decode this, and get the second flag !
$ echo "RU5TSUJTe28waEJ1dEhvV2QxZF95b3VGaW5kbTN9" | base64 -d
ENSIBS{o0hButHoWd1d_youFindm3}%
Feedback and last word !
Globally funny challenge. Thanks to the creator as well as the NorzhCTF staff for the event !
This write-up is written in a logical order. However, during the event, I found some elements before others and I couldn’t directly use them. For example, I found the anonymous FTP server long time before the necessary password for the ZIP archive.
Even if some initial statement elements were not clear (“on a server”, “inside files exchanged”) I liked the challenge and the global investigation.
o/