I’m sure you’ve already heard it thousand times, but questions about passwords on Internet are more than ever critical for your privacy and personal data. Nowadays, Internet is used for (almost) everything and by (almost) everyone, from the simple cooking website to your bank account, through social networks, marketing websites or even your mailboxes. It makes a lot of websites, account, and so, passwords.
This post won’t deal with the password complexity even if raising people awareness about this is important because tons of resources are available on Internet. No, this post will talk about the importance of using different passwords for every services. I’ll show you a little tool that could allow a bad guy to exploit the “password reuse”. Finally, some solutions will be presented.
The danger !
We won’t ever tell it enough, using the same password on different services is NOT a good idea. Actually, It’s dangerous for you.
The reason seems to be logical. If anyone can get access to one account, in one way, the entire set of data and accounts using this password is compromised.
Well, getting a password is not as hard as you think. Several tools and techniques are very efficient, depending on the target.
Furthermore, big companies databases stealing is not unusual, spreading users personal data over the Internet. These databases are then sold or published, offering the possibility for anyone to get users credentials. Here are some figures.
- Dropbox (2012) – 68 648 009 stolen accounts
- Dailymotion (2016) – 85,2 Millions stolen accounts
- LinkedIn (2012/2016) – 164 Millions stolen accounts
- Sony (PlayStation Network) en 2011 – 77 Millions stolen accounts including users bank informations
- OVH Kimsufi en 2017 (Same database has already been stolen 2 years ago) – 969 084 stolen accounts
- Adobe (2013) – 153 Millions stolen accounts
It should be noted that often, stolen password are hashed. It means that they are not stored in plain text inside the database. There are many hashing methods, resulting in more or less easy password cracking. However, once data are in the wild, password cracking is only about time !
Several websites can help you to know if your email address already leaked. You just have to give your email adress and the site compares it with his databases. https://haveibeenpwned.com/ is a great tool for that.
[Update December 2017] - A data breach compilation has been published this month. The main part of the compilation comes from known leak but there are some new ones. The 40Gb file contains 1.4 billion email addresses and passwords and is given with a small tool allowing you to search for email in few seconds, making this breach one of the biggest available resource for now. I’ve tested it and searched some things. Results, even if it includes some false positives, we can find interesting things. For example, I found one of my old email address 4 times, with 4 passwords I used on some services. If you want to test some of your email addresses, but you’re afraid of downloading the whole leak, please contact me by email or Twitter and I will check for you.
I let you imagine what impact it can have on you if one of your accounts is compromised by a data leak and you use the same password everywhere… ;)
Actually, instead of thinking about it, wouldn’t it be better to show a concrete scenario, in order to realise ?
Demonstration and Practical Scenario - Credmap discovery
These explanations aims both people interested in the technical part of the tool I’ll show and people outside the IT Security world but willing to see what is possible to do, why it’s dangerous and learn things.
NOTE : Understanding all the technical demonstration below is NOT necessary to understand the main stake. Text explanations are detailed for each picture or technical part.
There are plenty of tools to do some actions related to passwords. I’ll talk today about Credmap. The tool is developped by LightOS (Roberto Salgado) and available in a Github repository. Credmap is a “credential mapper”, it means that it will show a global view of a credentials couple (i.e username/password). The author warns about the fact that Credmap has been developped to raise people awareness about these dangers.
The tool works as the following. User provides a username and/or an email address with a password and then, according to settings and targetted websites, Credmap will try to authenticate to the different websites. It’s pretty simple but it allows to automate the process and get fast results for many websites.
To show you how it works, I’ve created accounts on Twitter, Spotify, Github and Laposte with the following informations :
- Username : anona17
- Email address : anona17@gmx.fr
- Password : Anona1337
Well ! We have our test accounts. Now, let’s download Credmap through the official Github repository. Credmap is written in Python. I’ll skip details about how to start a program with Python. We just type “./credmap.py -h” to display the help menu (Executing the program with ./credmap.py and uses “-h” as an option to display help).
$ ./credmap.py -h
. .IIIII .II
I123456IIII. I II . II..IIIIIIIIIIIIIIIIIIII
. .IIIIII II IIIIIIHUNTER2IIIII I.
.IIIII.III I IIIIIIIIIIIIIIIIIIIIIII
.IILOVEII II .IIIII IIIIIIIIIIII. I
IIIIII IIII I IISECRETIIIIIII I
.II IIIIIIIIIIIII IIIIIIIII
I. .IIIABC123IIII I II I
.IIII IIIIIIIIIIII . I
IIIII. IIIIII . I.
IIGODIII IIIII ..I II .
IIIIII IIII... IIII
IIII III. I IISEXII
III I I III
II I .
I
credmap v0.1-c4cd03d (https://github.com/lightos/credmap/)
Usage: credmap.py --email EMAIL | --user USER | --load LIST [options]
Options:
-h/--help show this help message and exit
-v/--verbose display extra output information
-u/--username=USER.. set the username to test with
-p/--password=PASS.. set the password to test with
-e/--email=EMAIL set an email to test with
-l/--load=LOAD_FILE load list of credentials in format USER:PASSWORD
-f/--format=CRED_F.. format to use when reading from file (e.g. u|e:p)
-x/--exclude=EXCLUDE exclude sites from testing
-o/--only=ONLY test only listed sites
-s/--safe-urls only test sites that use HTTPS
-i/--ignore-proxy ignore system default HTTP proxy
--proxy set proxy (e.g. "socks5://192.168.1.2:9050")
--list list available sites to test with
--update update from the official git repository
Examples:
./credmap.py --username janedoe --email janedoe@email.com
./credmap.py -u johndoe -e johndoe@email.com --exclude "github.com, live.com"
./credmap.py -u johndoe -p abc123 -vvv --only "linkedin.com, facebook.com"
./credmap.py -e janedoe@example.com --verbose --proxy "https://127.0.0.1:8080"
./credmap.py --load creds.txt --format "e.u.p"
./credmap.py -l creds.txt -f "u|e:p"
./credmap.py -l creds.txt
./credmap.py --list
Ok, we can see that the program needs a username and/or email address, password and a list of website we want to test. It’s possible to use others options but they won’t be approched today. In order to see the available websites list, we can use the “–list” option.
$ ./credmap.py --list
. .IIIII .II
I123456IIII. I II . II..IIIIIIIIIIIIIIIIIIII
. .IIIIII II IIIIIIHUNTER2IIIII I.
.IIIII.III I IIIIIIIIIIIIIIIIIIIIIII
.IILOVEII II .IIIII IIIIIIIIIIII. I
IIIIII IIII I IISECRETIIIIIII I
.II IIIIIIIIIIIII IIIIIIIII
I. .IIIABC123IIII I II I
.IIII IIIIIIIIIIII . I
IIIII. IIIIII . I.
IIGODIII IIIII ..I II .
IIIIII IIII... IIII
IIII III. I IISEXII
III I I III
II I .
I
credmap v0.1-c4cd03d (https://github.com/lightos/credmap/)
- en.wikipedia.org
- amazon.com
- trakt.tv
- instagram.com
- netflix.com
- facebook.com
- spotify.com
- wunderlist.com
- github.com
- laposte.net
- bitbucket.org
- airbnb.com
- live.com
- imgur.com
- twitter.com
- reddit.com
- stackoverflow.com
- pastebin.com
- yahoo.com
- linkedin.com
- zoho.com
- groupon.com
- pinterest.com
- digitalocean.com
- soundcloud.com
- foursquare.com
- ebay.com
- scribd.com
- yelp.com
- vimeo.com
NOTE : The website “Laposte.net” is not in the default list, but I’ll come back later on it.
Now that we know the tool is working, let’s try to use it. Imagine that your username/password has leaked from one of the various website you registered. Someone is getting these informations : username (anona17), email address (anona17@gmx.fr) and password (Anona1337).
We will try to use Credmap on various websites and see what happens.
$ ./credmap.py -u anona17 -e anona17@gmx.fr -p Anona1337 --only "twitter.com, github.com, spotify.com, reddit.com"
. .IIIII .II
I123456IIII. I II . II..IIIIIIIIIIIIIIIIIIII
. .IIIIII II IIIIIIHUNTER2IIIII I.
.IIIII.III I IIIIIIIIIIIIIIIIIIIIIII
.IILOVEII II .IIIII IIIIIIIIIIII. I
IIIIII IIII I IISECRETIIIIIII I
.II IIIIIIIIIIIII IIIIIIIII
I. .IIIABC123IIII I II I
.IIII IIIIIIIIIIII . I
IIIII. IIIIII . I.
IIGODIII IIIII ..I II .
IIIIII IIII... IIII
IIII III. I IISEXII
III I I III
II I .
I
credmap v0.1-c4cd03d (https://github.com/lightos/credmap/)
[i] Loaded 4 sites to test.
[i] Starting tests at: "09:55:38"
[*] Testing "Spotify"...
[+] Credentials worked! Successfully logged in.
[*] Testing "Github"...
[+] Credentials worked! Successfully logged in.
[*] Testing "Twitter"...
[+] Credentials worked! Successfully logged in.
[*] Testing "Reddit"...
[+] Succesfully logged into 3/4 websites..
[+] An overall success rate of %75.
[+] The provided credentials worked on the following websites: Spotify, Github, Twitter
[i] Finished tests at: "09:55:42"
Great ! On “Spotify”, “Github” and “Twitter”, credentials worked ! In concrete terms, it means that you juste gave these 3 accounts to the hacker. He now can authenticate with the same credentials thanks to the tool that showed him it was valid. We can see that for “Reddit” it didn’t work, which is completely normal because we don’t have such account on the website. It’s possible now to see further by trying to think like the bad guy. By seeing that the target user has used the same password on several services, we can imagine that these same credentials are used elsewhere and then go for it manually.
Another tool specificity is the possiblity to manually add websites. Indeed, the website list is available under the “websites” folder and each website corresponds to one XML file. For example, here is the “spotify.com.xml” content.
<properties>
<name value="Spotify" />
<description value="Online music streaming service." />
<login_url value="https://accounts.spotify.com/api/login" />
<invalid_http_status value="400" msg="Probably invalid credentials..." />
<valid_password value="{"displayName":"" />
<invalid_password value="{"error":"errorInvalidCredentials"}" />
<headers value="Referer=https://accounts.spotify.com/en-US/login" />
<cookies value="__bon=MHwwfC0zMDc2NTg4NzR8LTEyOTIxNjcyNzA4fDF8MXwxfDE=" />
<username_or_email value="both" />
<login_parameter value="username" />
<password_parameter value="password" />
<csrf_token_name value="csrf_token" />
<csrf_url value="https://accounts.spotify.com/en-US/login" />
<csrf_setcookie value="csrf_token=(?P<token>[^\s]+)" />
<data value="remember=false&username=&password=&csrf_token=" />
</properties>
Details for every fields are available in the documentation, on the Github repository. So, it’s possible to add websites, like for example, Laposte.
<properties>
<name value="Laposte.net" />
<description value="Laposte.net is a french mail provider" />
<login_url value="https://m.laposte.net/api/v1/auth/" />
<valid_password value="Réception" />
<invalid_http_status value="401" msg="expected" />
<invalid_password value="Erreur de saisie du login ou du mot de passe." />
<invalid_account value="Erreur de saisie du login ou du mot de passe." />
<valid_response_header value="MLPN_AUTH_TOKEN="/>
<headers value="content-type=application/json\nReferer=https://m.laposte.net/login" />
<username_or_email value="username" />
<login_parameter value="login" type="json"/>
<password_parameter value="password" type="json"/>
<data value="{"login":"","password":""}" />
</properties>
Let’s try now with the previous credentials.
$ ./credmap.py -u anona17 -e anona17@gmx.fr -p Anona1337 --only "laposte.net" . .IIIII .II
I123456IIII. I II . II..IIIIIIIIIIIIIIIIIIII
. .IIIIII II IIIIIIHUNTER2IIIII I.
.IIIII.III I IIIIIIIIIIIIIIIIIIIIIII
.IILOVEII II .IIIII IIIIIIIIIIII. I
IIIIII IIII I IISECRETIIIIIII I
.II IIIIIIIIIIIII IIIIIIIII
I. .IIIABC123IIII I II I
.IIII IIIIIIIIIIII . I
IIIII. IIIIII . I.
IIGODIII IIIII ..I II .
IIIIII IIII... IIII
IIII III. I IISEXII
III I I III
II I .
I
credmap v0.1-c4cd03d (https://github.com/lightos/credmap/)
[i] Loaded 1 site to test.
[i] Starting tests at: "10:25:08"
[*] Testing "Laposte.net"...
[+] Credentials worked! Successfully logged in.
[+] Succesfully logged into 1/1 websites..
[+] An overall success rate of %100.
[+] The provided credentials worked on the following website: Laposte.net
[i] Finished tests at: "10:25:08"
Nice ! How to add websites to our weapo…tool! and making it more powerfull/dangereous ;)
That’s how someone can start from a data leak (which is absolutely not your fault) to a complete accounts theft (and here, it’s your fault !).
SOlution
Unfortunately, these “vulnerabilities” are purely humans… That’s what it makes them so dangerous for you. This is not related to a vulnerability in the website you use, but related to a behavior on the Internet. That said, it’s kinda easy to counter that kind of attack. There are several important things, but one of the most important rule is uniqueness : your password must be unique on each website/service.
[Update December 2017] - Then, several recommandations must be taken into consideration. Until recently, the rule was to choose complex passwords. For more informations, you can refer to the ANSSI recommandations about password security. But now, NIST (National Institute of Standards and Technology) recommandations has changed and advice to use “passphrase” instead of complex passwords. The idea if the following : A complex password can be very difficult to memorize for a human and can be simple to guess for a machine, whereas a passphrase is easy to remember and harder to guess. Just check the following drawing to understand that.
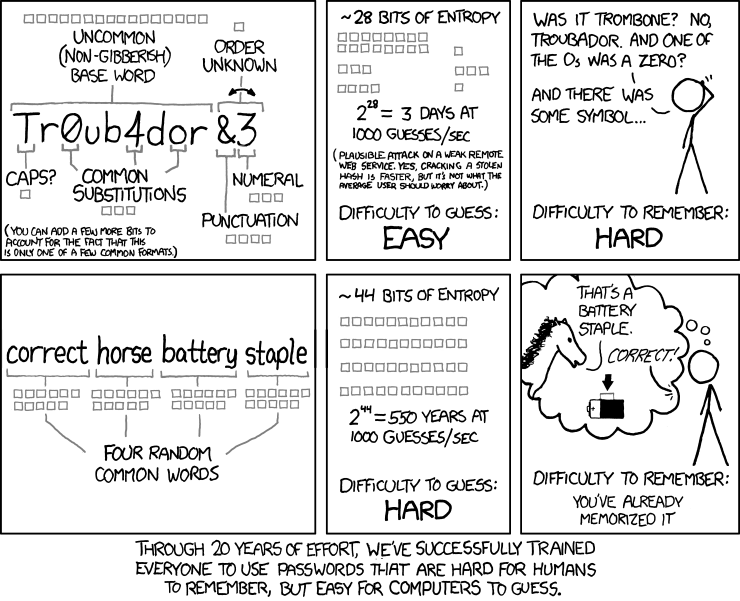
However, I’ll add something. If you don’t comfortable with memozizing many passwords or even a mental method to remember them, other solutions are available.
Indeed, you can use a “Password Manager”. These software, like KeepassX or Keepass give you the opportunity to store your passwords in a secure database on your computer. To unlock it, you only need one password, the one you chose for the database. It’s pretty practical. However, take care ! If you forget your main password, it could be very difficult to recover your credentials… But there is ony one password to remember, and it’s still better than write down all your passwords on your desktop… ;)
Pour plus d’informations sur ces logiciels, voici un petit tutoriel expliquant comment mettre en place Keepass sur son ordinateur : https://craym.eu/tutoriels/utilitaires/keepass.html
Conclusion
We just saw how much it’s dangerous to use the same password on different services and that data leak are far more regular than we believe. Then, I showed a little tooln designed to exploit the password reuse and finally, we talked about different existing solutions to protect yourself but mostly to learn good practices in term of account protection.
It effectively requires some work to search, learn and do the necessary, but ask yourself : Do you care about your accounts, about your numerical identity ? And ask yourself how many services are using the same password ? What can a hacker take and steal if he gets this door opener ? I’m pretty sure that answers bring you to awareness and reaction !
Ah, last thing, don’t think it only happens to other people. As we saw, you’re not responsible for data leak, and that’s several thousands or millions accounts regularly.
You are now aware about the risk of using the same password and you don’t have pretext anymore to not update yours, and so, to protect yourself !
NOTE : The Credmap author is currentily working on another tool, a kind of credmap 2.0. But currently, Credmap is still functionnal ! Stay tuned if you’re interested.
If you have any question, please don’t hesitate to contact me through Twitter ;).