A little lighter post this time, dealing with connected internet boxes, and specifically the Miami Bboxes (which is a French ISP). Indeed, having one of these boxes, I wondered what I could find from a privacy point of view and what a basic and curious user could do with parameters. We will therefore see here that a certain number of default parameters are activated and that it is possible to act on them. I should point out that no box was mistreated in the context of these experiments : D.
Even if I didn’t get the opportunity to test on other devices, I suppose that the same type of parameters exist. Furthermore, it is important to note that this is only an overview. More things are probably possible. In the context of this post, the purpose is simply to give information that this exists. But if like me, you only use a few advanced features of these boxes, then taking a look at the following lines can be interesting…
Remote Tracking
Tracking
The first element I focused on was tracking as it is called in the parameters. To access the this one, go to the “Settings” and then in the “Preferences” section go to the “Suggestions” section.
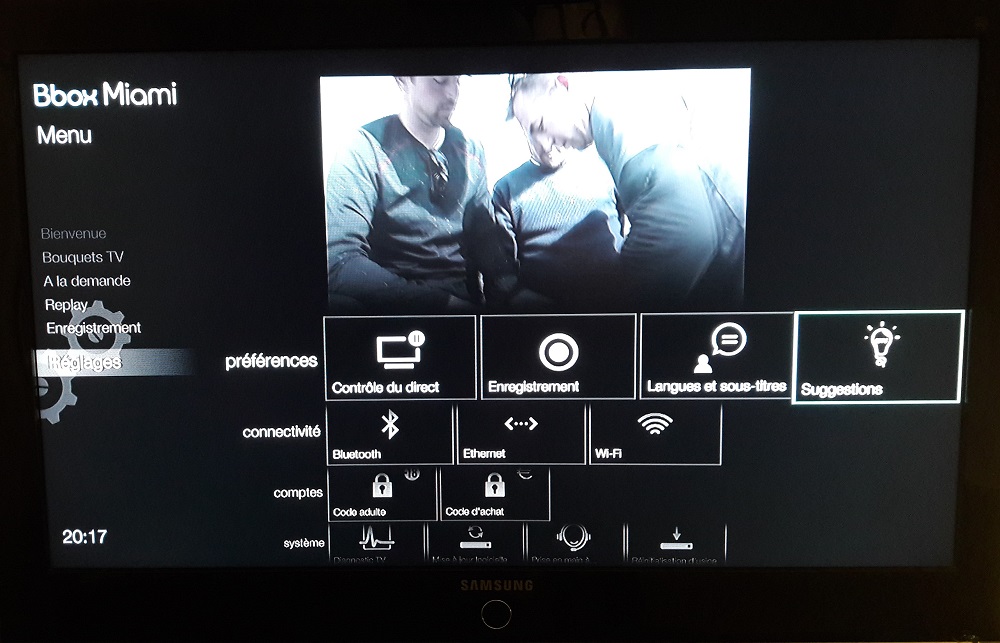
Two parameters are available here, including the famous “Tracking”. This setting, enabled by default, seems to be used to provide information to your ISP (“track” you) about the programs viewed and actions performed on the device in order to customize the offer and thus provide potentially more appropriate content. Problem, we don’t know what is actually collected. So, if you are not interested in this feature, disabling this tracking allows you to start limiting the information leak from your life.
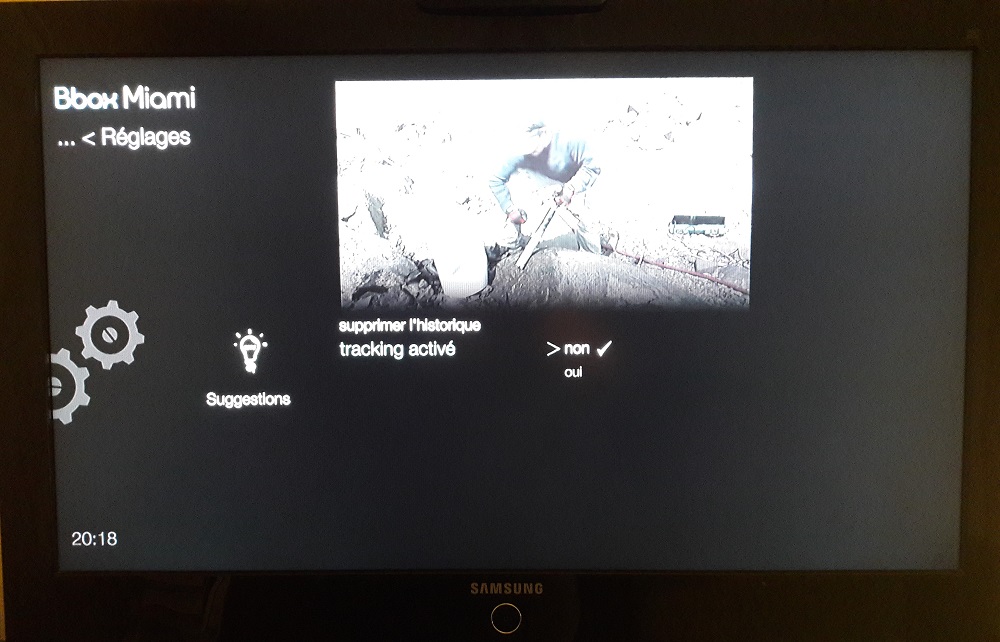
User history
Other officially used element to provide you with more personalized content, history of programs viewed, applications used, etc. This data is used in the same way as the tracking described above. So, again, if you don’t want to be influenced on which programs you should watch or if the recommendations are not used, in a privacy concern, you can regularly delete the history.
Casted data
It is possible with this type of device to “cast” content. It consists in broadcasting content from another device to the Bbox. For example, you can stream a YouTube video from your phone directly to your TV. Very practical functionality! Nevertheless, looking through the options related to this, we notice that it is possible to choose if we want some of these data to be sent to Google as well! The functionality is also used to send error reports, which can be useful. This parameter is accessible via the complete device settings, accessible from the application selection menu.
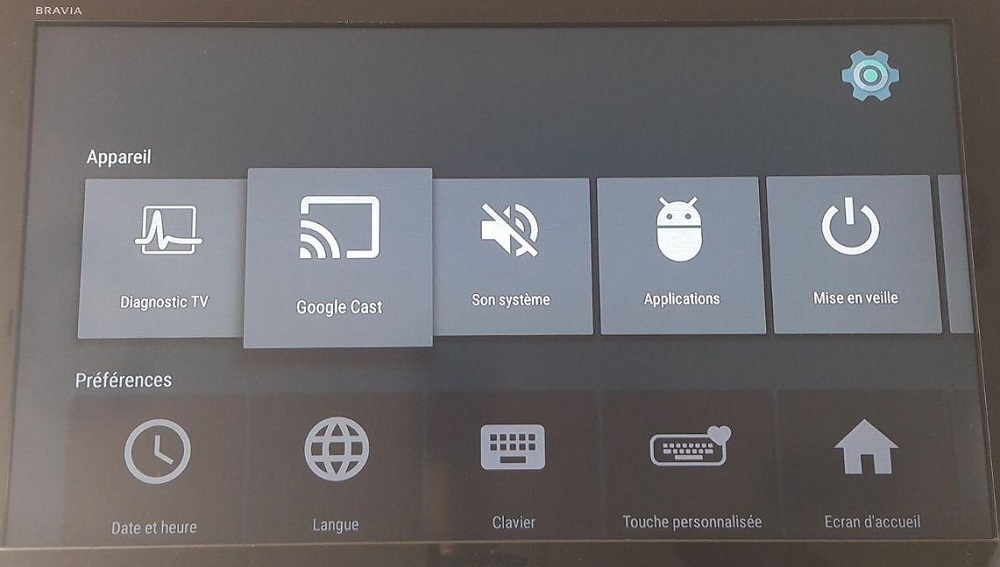
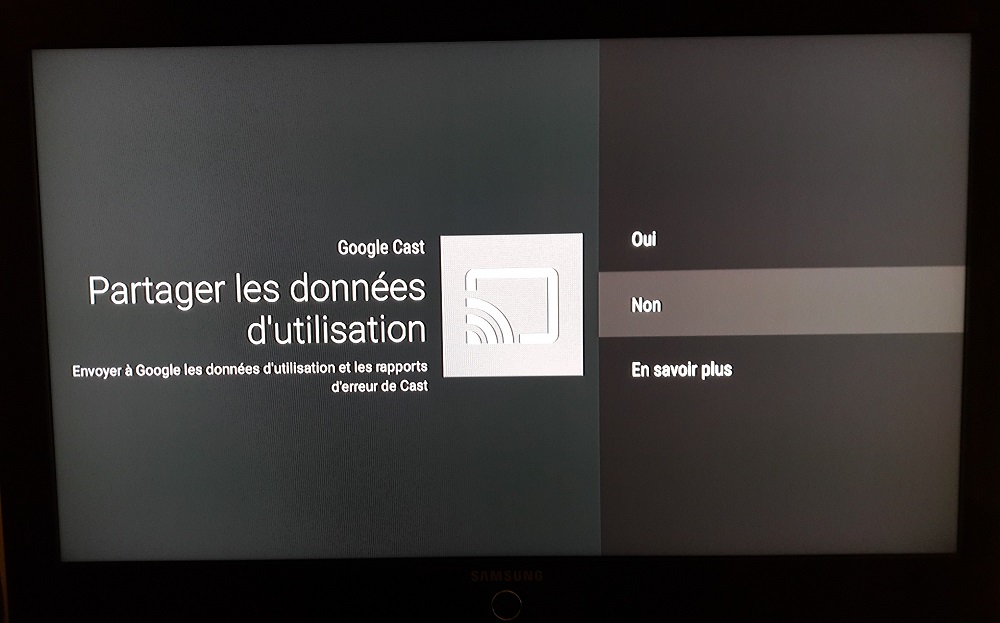
Nevertheless, is it worth it? It’s up to you to judge! In any case, it is also possible to limit this by disabling sharing with Google.
Voice control
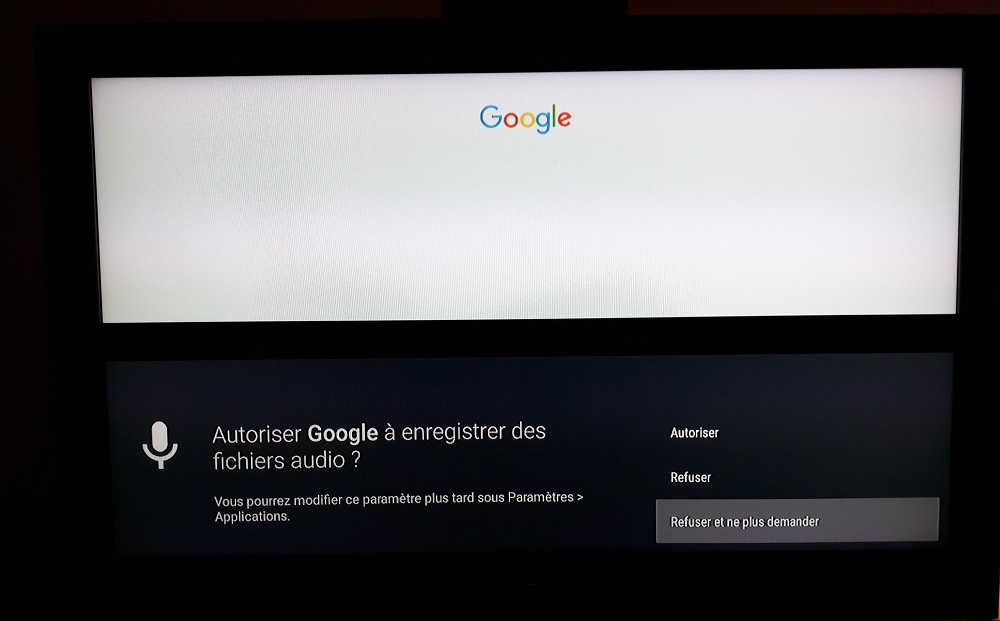
A major technological progress in recent years, highlighted by all media, the voice control. As technological equipment, the connected boxes are also equipped with it. It is possible to configure it in the box settings. When activating it, you must be aware that the microphones used are likely to be listening at any time, in order to be able to detect an “Ok Google”. Therefore, it is also possible that the sound of the piece is recorded.
From that moment on, two ways of thinking. If this feature, which remains convenient, is used, then it is necessary to leave this setting enabled. However, if you don’t use the it and I think most people are in this situation, then why let one more device record your conversations all day long?
Application
Like any system running with an Android version, it is possible to use a multitude of applications directly on a connected box, downloadable via the Play Store. The applications installed on the box are accessible from the general settings in the “Applications” tab.
Default installed applications
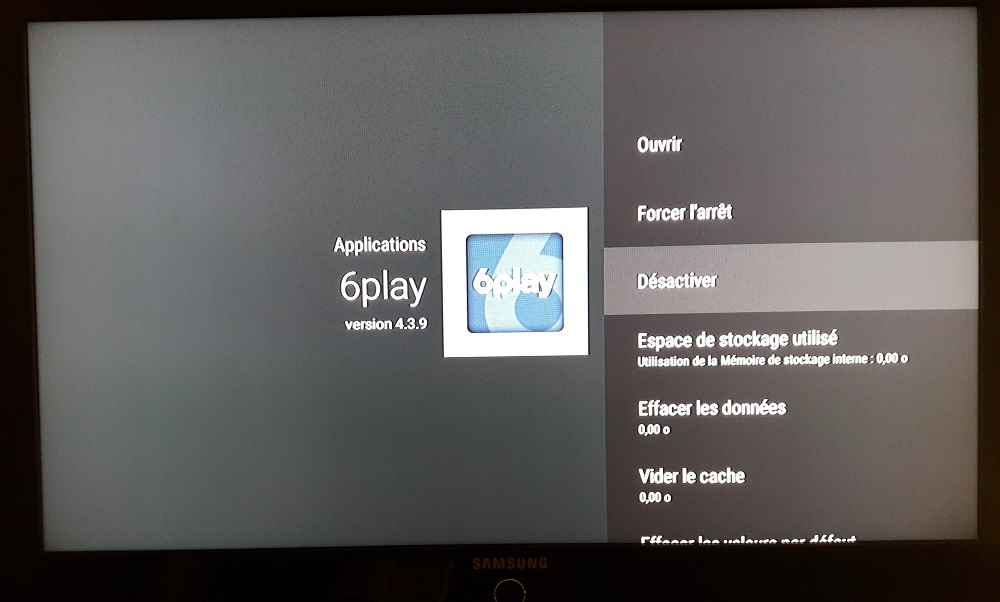
But like any Android system, many (useless?) applications are present and installed by default. It will be possible to uninstall some of them completely, while others will simply be deactivatable. Better than nothing, because it will prevent them from acting and restrict their access (this point will be explained in the next section). So, you are free to choose which applications you want to disable.
Story of the day: The “Dorcel Store” application is for example installed by default on Miami Bboxes… :D
Right management
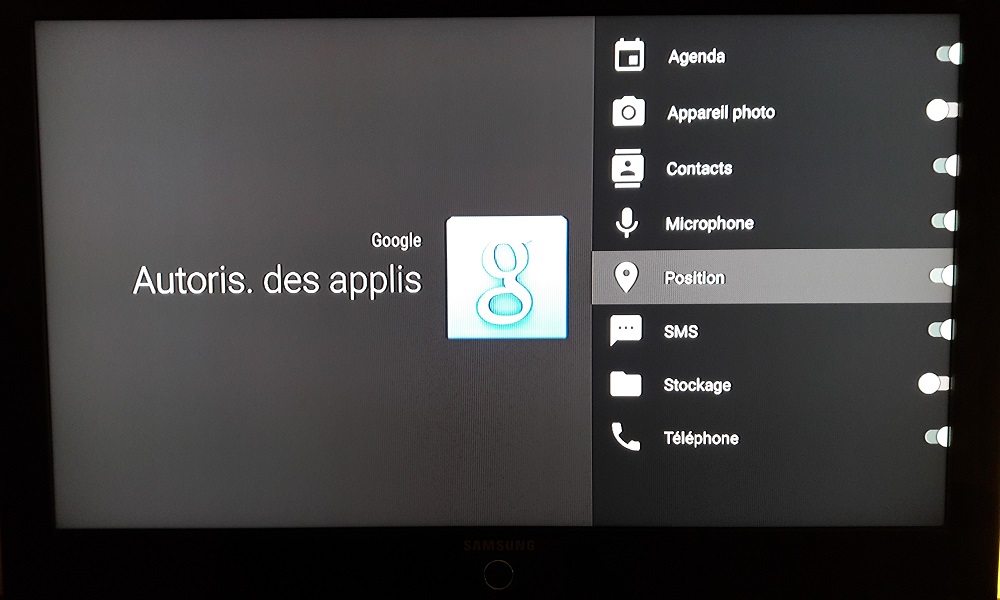
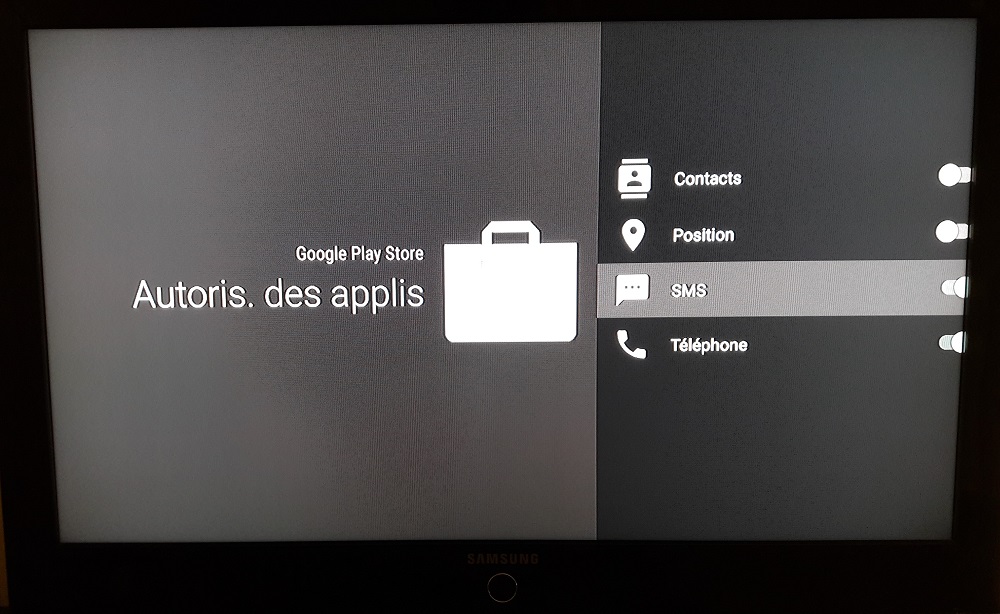
One thing that is one of the most sensitive point concerning applications. This applies to all systems running Android and more broadly, to most computer systems. We’re talking about right management.
Under Android, application permissions are divided into 8 or 9 categories (see list below for Miami Bbox). This includes, for example, the right to access SMS, camera, microphone, contacts, etc.
Some applications need some permissions, of course, but some applications do not hesitate to ask for permissions that they would not normally need. For example, why would the Netflix application need to access your camera?
All permissions for each application are adjustable according to your wishes and it is IMPERATIVE to check them for each application you use or install (this also applies to smartphones, but a more detailed article will come in a few weeks).
A message indicating that an application may no longer work if some permissions are removed may appear and this is true. However, if you leave the appropriate authorisations in a logical and rational way, you should not have any problems.
Quick word about WiFi
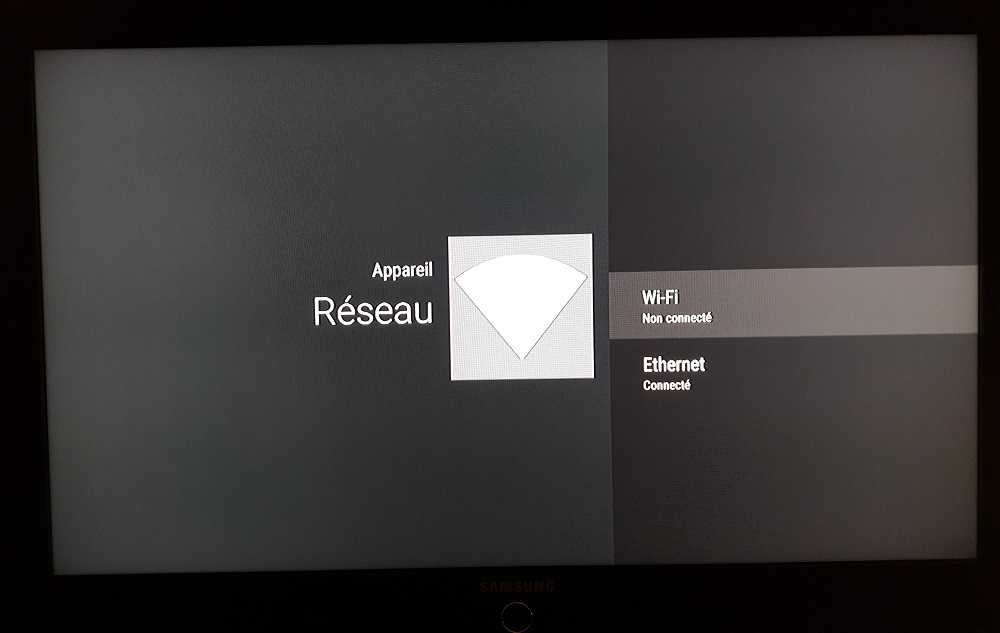
By default, in most houses, the connected box will be installed next to the “classic” box (the router). Thus, these two devices will be connected by Ethernet cable. Therefore, and unless you have special needs, it is not necessary to enable WiFi on the Miami Bbox (device settings (settings) > connectivity).
Conclusion
This article only scratches the surface of the problem and it is clear that the few examples seen will not revolutionize anonymity and privacy. Nevertheless, these are small steps that may interest some people and may lead others to learn more about the subject or to further research. Thus, these few points present very simple measures to implement, since the functionalities are not used, in order to limit as much as possible leak of your consumption data to the outside world, in order to prevent these data from being used for other purposes, for example…