Since the release of the Windows 10 operating system, many questions about user privacy have been raised. Indeed, even if our data were already collected before, Microsoft has opened their communication on the data collection with Windows 10. It allows mani people to open their eyes and become aware of things happenin.
However, it is possible through various small manipulations and configurations to limit the personal data leak that are collected by Microsoft. This can be done through Group Policy Objects and we will discover them in this post. I will give you some examples so that you can have an idea of how they are used. I would like to take this opportunity to say a word about the ANSSI (French National Agency for System Security) which regularly publishes guides to good practice on digital good pratices. Configurations showed in this article are taken from their guide “Concerns about privacy and data confidentiality in Windows 10” and have been compiled by @Gouzou, many thanks for his help!
[Preliminary Note 1] This article will be updated (more or less) regularly to add or remove some interesting parameters.
[Preliminary Note 2] GPO management is only possible with a Pro, Enterprise or Integral version of Windows 7, 8.1 or 10. However, it seems possible to install the editor on more traditional versions (Home). I never tested it, so I just can’t tell if it’s true or not.
GPO (Group Policy Objects)
What the hell is that ?
Group Policy Objects (GPOs) are centralized management functions for Windows. They are used in company networks, composed of many computers. By using them, you can easily deploy parameters throughout the fleet or configure some network and security parameters, etc. There are several hundred of GPOs, making it possible to administer a large number of things.
Even if this system is mainly used in company networks, there is a local version on every computers, allowing each administrator to define parameters for his machine, we talk of local policies.
Inside a company, it is possible to set up both local policies (for your PC only) and group policies (for the entire IT infrastructure). However, parameters are in conflict, the group policy will take priority and be applied, intead of local Setting s.
In case of a personal computer, no worries . I won’t go deeper on GPOs because it could quickly become complex and the goal is not to go in depth.
How does it work ?
In practice, all GPOs are managed in the same place, in the group policy editor. A significant number of parameters are available and to choose one value when we have the choice. For example, it is possible to activate or deactivate this account for the parameter “Accounts : Guest account status” . Below is a screenshot illustrating what the editor looks like.
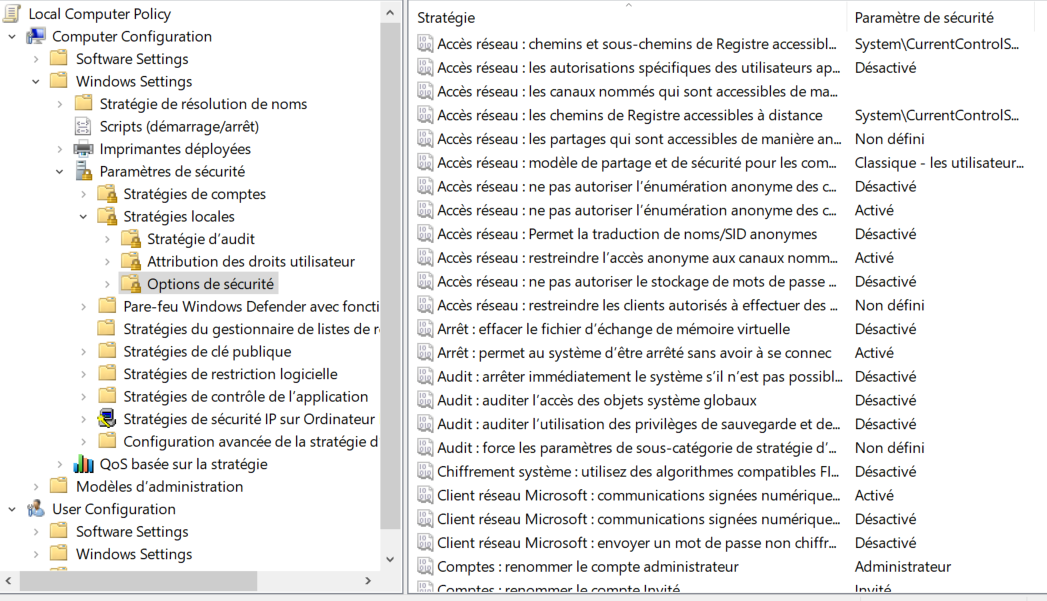
Inside a company’s IT system, group policies are managed in the Active Directory domain controllers. These are the servers used to rule the infrastructure.
What about my computer ?
As mentioned above, there is a local version of the policy editor. We are talking here about the local strategy editor. It looks exactly like the GPO editor on Windows servers, but the Setting s you set are only applied to your computer. Pretty nice when you just want to protect your PC !
In order to find the editor, two ways:
- Use the Windows search bar and type “Group Policy” or “Group Strategies”. It is necessary to run the program as an administrator (right click on it and then “run as administrator”);
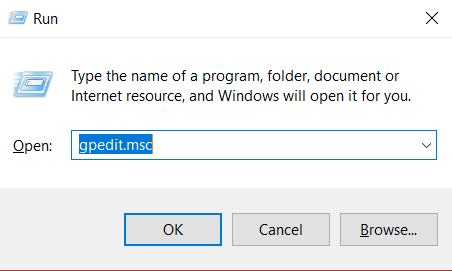
- Use the Windows application to launch a program. To do this, use the “Windows” keys (the key with the Windows icon) + “R” then enter “gpedit.msc”.
When done, you end up with the same editor. And we can start searching :).
Application Case - GPO Configuration
In accordance with ANSSI documents and the parameters that @Gouzou has extracted from their documents, there are several categories of parameters that are interesting to look at for personal protection purposes. You should note, however, that everything shouldn’t be taken as done. Indeed, recommendations presented here can guide you in the configuration of your system but it is up to you to define what you want to protect. I strongly encourage you to read the description of each parameter to find out what it is about.
Path explanations
During the post, each parameter will be accessible via a “path”. For example:
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/Data Collection and Preview Builds
It corresponds to the different categories and sub-categories you can see in the editor.
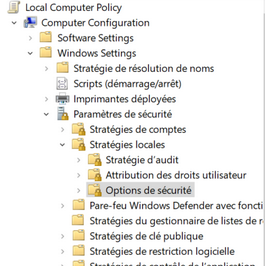
Once you have reached a parameter, simply click on it and then choose whether to enable it, disable it and add any options.
Telemetry, Search and Integrated Tools
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/Data Collection and Preview Builds
| Setting | State | Options |
|---|---|---|
| Allow telemetry | Enabled | 0 (Disabled) ou 1 (Basic) |
| Do not show feedback notifications | Disabled | - |
| Toggle user control over Insider Build | Disabled | - |
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/Windows Defender Antivirus/MAPS
| Setting | State | Options |
|---|---|---|
| Configure local Setting override … MAPS | Disabled | 0 (Disabled) ou 1 (Basic) |
| Send file samples whe further analysis is required | Disabled | - |
| Join Microsoft MAPS | Disabled | - |
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/Search
| Setting | State | Options |
|---|---|---|
| Allow Cortana | Disabled | - |
| Allow Cortana above lockscreen | Disabled | - |
| Allow indexing of encrypted files | Disabled | - |
| Do not allow web search | Enabled | - |
| Set what information is shared in Search | Enabled | Anonymous infos |
| Don’t search the web or display web results in Search | Enabled | - |
| Allow Cloud Search | Disabled | - |
| Allow Cortana Page in OOBE on an AAD account | Disabled | - |
User Experience
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/Location and Sensors
| Setting | State | Options |
|---|---|---|
| Turn off location | Disabled | - |
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/Windows Error reporting
| Setting | State | Options |
|---|---|---|
| Disable Windows error reporting | Enabled | - |
| Automatically send memory dumps for OS-generated error reports | Disabled | - |
| Do not send additional data | Enable | - |
Local Computer Policy/Computer configuration/Administrative Templates/Control Panel/Regional and Language Options
| Setting | State | Options |
|---|---|---|
| Allow input personalization | Disabled | - |
Local Computer Policy/Computer configuration/Administrative Templates/Control Panel/Regional and Language Options/Handwriting personalization
| Setting | State | Options |
|---|---|---|
| Turn off automatic learning | Enabled | - |
Local Computer Policy/Computer configuration/Administrative Templates/System/Internet Communication Management/Internet Communication Setting s
| Setting | State | Options |
|---|---|---|
| Turn off Help and Support Center “Did you know ?” content | Enabled | - |
| Turn off handwriting personalization data sharing | Enabled | - |
| Turn off Windows Customer Experience Improvement Program | Enabled | - |
| Turn off hanwriting recognition error reporting | Enabled | - |
| Turn off access to the Store | Enabled | - |
| Turn off Windows Error reporting | Enabled | - |
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/Cloud Content
| Setting | State | Options |
|---|---|---|
| Turn off Microsoft consumer experiences | Enabled | - |
| Do not Windows tips | Enabled | - |
Universal Apps
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/App Privacy
| Setting | State | Options |
|---|---|---|
| Let Windows apps access […all…] | Enabled | Ne jamais autoriser |
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/Store
| Setting | State | Options |
|---|---|---|
| Only display the private store within the Windows Store App | Enabled | - |
| Turn off the Store application | Enabled | - |
| Disable all apps from Windows Store | Enabled | - |
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/System/User Profiles
| Setting | State | Options |
|---|---|---|
| Turn off advertising ID | Enabled | - |
| Do not log users with temporary profiles | Enabled | - |
Local Computer Policy/Computer configuration/Windows Setting s/Security Setting s/Local Policies/Security Options
| Setting | State | Options |
|---|---|---|
| Accounts : Block Microsoft accounts | Enabled | Users can’t add or log on with Microsoft Accounts |
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/OneDrive
| Setting | State | Options |
|---|---|---|
| Prevent the usage of OneDrive for files storage | Enabled | - |
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/Text Input
| Setting | State | Options |
|---|---|---|
| Improve inking and typing recognition | Disabled | - |
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/Windows Defender Application Guard
| Setting | State | Options |
|---|---|---|
| Turn on Windows Defender Application Guard in Enterprise | Enabled | - |
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/Push To Install
| Setting | State | Options |
|---|---|---|
| Turn off Push to Install service | Enabled | - |
Local Computer Policy/Computer configuration/Administrative Templates/System/OS Policies
| Setting | State | Options |
|---|---|---|
| Allow publishing of User Activities | Disabled | - |
| Allow upload of User Activities | Disabled | - |
| Enable activity feeds | Disabled | - |
Local Computer Policy/Computer configuration/Administrative Templates/Windows Components/Windows Game Recordings and Broadcasting
| Setting | State | Options |
|---|---|---|
| Enables or disables Windows Game Recordings and Broadcasting | Disabled | - |
Bonus - Set hard times for pre-installed Microsoft Apps
You probably already had to deal with it, when you buy a new computer, many applications are installed by default. Even if some of them are useful, you’ll likely want to delete some of them. However, Windows doesn’t let us do it so easily! Indeed, the “uninstall” option is not available….
But it is still possible to delete some of them ! Unfortunately, it will not be possible to uninstall them all (Cortana, for example). Once again, it is up to you to judge what you’ll need or not :).
The next few lines may scare the least technicals among you. Nevertheless, don’t panic, don’t leave at the slightest line of code, everything is explained !
We’ll start by opening a Powershell interpreter. Roughly speaking, it is a terminal in which we can enter commands. Look for the “Powershell” program and launch it as administrator (right click > Run as administrator). A blue terminal, like this one, should appear.
Thereafter, 3 commands will be necessary.
First, we will list the installed applications. This is done using the following command. It will list applications and display a lot of information about them.
Get-AppxPackage
For readability reasons, we likely would list applications and display only their full name. This can be done with the command below.
Get-AppxPackage | Select Name, PackageFullName
Then, simply tell the computer to get an application and a second “Remove-AppxPackage” command is added to tell it to delete the application.
Get-AppxPackage -allusers *3dbuilder* | Remove-AppxPackage
Command description :
- GetAppxPackage = List of installed applications ;
- -allusers = Indicates that the command will cover all computer users;
- *zunevideo* = Name of the application. We use two “*” to indicate that we are simply looking for the expression between the two symbols in the result of the list, in order to select the right application. In our case, we will uninstall all applications containing “zunevideo” in their name;
- | = Allows to link the first command to a second one;
- Remove-AppxPackage = Indicates that you want to delete the selected application.
Using that, you can delete many applications. I invite you to consult this link for more information and a list of applications that can be deleted.
Conclusion
In conclusion of this post, I would like to remind you that many things are possible in order to personalize your computer and limit information leaks, but that you do not necessarily have to take everything like that. Indeed, more than implementing recommendations (even those in this article), it is important to be informed, aware and to try to understand at least the overall behavior. Each person or company has different security and privacy needs, leaving a multitude of possible configurations. It’s up to you to find the right one!
As always, if you have any questions, feel free to contact me on Twitter ! ;)